Dive into the Summer ’24 Release
As an admin, you can help your organization succeed by staying up to date with the latest Salesforce releases and getting familiar with product enhancements.
Check out the Summer ’24 release notes for a list of new features and available updates.

Did you find this helpful?
Help us enhance your experience.

Product Area
Feature impact.
- Start a New Trial
- Delete Trial Data
- Plan Your Salesforce Rollout
- Manage Information About Your Company
- Allow the Required Domains
- Allow Network Access for News, Account Logos, and Automated Account...
- Web Request Limits
- User Interface Settings
- Find Items in Setup with Advanced Setup Search (Beta)
- Setup Search Results Page (Beta)
- Set a New Default Home Page
- Assign Custom Home Pages to Specific Apps and Profiles
- Lightning Experience Home Permissions and Settings
- Lightning Experience Record Page Views
- Set the Default Lightning Experience Record Page View
- Activities View
- Set the Default Activities View
- Select Languages for Your Org
- Adopt the ICU Locale Formats
- Determine Whether Your Org Uses ICU or JDK Locale Formats
- Considerations for Adopting the ICU Locale Formats
- Create a SOQL Query
- Create a Custom Object for a Report
- Identify Locales in Use by User
- Identify Changes to Your Locales with ICU
- Differences Between JDK and ICU Locale Formats
- Enable the ICU Locale Formats
- Check for API Versions
- Update the API Version
- Use Locale-Neutral Methods in Code
- Example Code with Locale-Formatted Data
- Update Your Integrations for New Locale Formats
- ICU Locale Format Migration Tests
- Supported Number, Name, and Address Formats (ICU)
- Supported Currencies (ICU)
- Supported Number, Name, and Address Formats (JDK)
- Supported Date and Time Formats (JDK)
- Supported Currencies (JDK)
- Set Your Currency Locale
- Set Your Corporate Currency
- Set Your Personal Currency
- Edit Conversion Rates
- Supported Time Zones
- Add Local Name Fields to a Page Layout in Salesforce Classic
- Add Local Name Fields to a Page Layout in Lightning Experience
- Enable the Japanese Imperial Calendar
- Set the Fiscal Year
- Customize the Fiscal Year Structure
- Customize the Fiscal Year Labels
- Choose a Custom Fiscal Year Template
- Define or Modify a Custom Fiscal Year
- Turn Einstein Features On or Off
- Einstein and Data Usage in Service Cloud and Lightning Platform
- Einstein and Data Usage in Commerce Cloud
- Set Up Einstein Search
- Autocomplete Addresses
- Considerations for Autocompleting Addresses
- Integration Values for State and Country/Territory Picklists
- Configure State and Country/Territory Picklists
- Standard Countries and Territories for Address Picklists
- Edit State, Country, and Territory Details
- State and Country/Territory Picklists and the Metadata API
- Prepare to Scan State, Country, and Territory Data and Customizations
- Scan State and Country/Territory Data and Customizations
- Prepare to Convert State, Country, and Territory Data
- Convert State and Country/Territory Data
- Enable and Disable State and Country/Territory Picklists
- State, Country, and Territory Picklist Fields
- State and Country/Territory Picklist Field-Syncing Logic
- State and Country/Territory Picklist Error Messages
- Let Users See Report Headers While Scrolling
- Help Users Find Dashboards Quickly
- Let Users Post Dashboard Widgets in Chatter
- Exclude the Confidential Information Disclaimer from Reports
- Let Users Attach Files to Report Subscriptions
- Hide the Embedded Salesforce Classic Report Builder in Lightning...
- Let Users Subscribe to Report Notifications
- Customize Report and Dashboard Email Notifications
- Create a Custom Report Type
- Add Child Objects to Your Custom Report Type
- Design the Field Layout for Reports Created from Your Custom Report...
- Manage Custom Report Types
- Limits on Report Types
- Bulk Move Reports or Dashboards with Metadata API
- Set Up Historical Trend Reporting
- Upgrade the Report Wizard
- Manage Release Updates
- Security Alerts
- How Divisions Work
- Set Up Divisions
- Create and Edit Divisions
- Transferring Multiple Records Between Divisions
- Change the Default Division for Users
- Reporting With Divisions
- Read-Only Mode
- 5 Minute Upgrades
- Check for Desktop Client Updates
- Permissions for UI Elements, Records, and Fields
- Deactivate a Developer Edition Org
- Developer Org Expiration
- Give Your Billing Users Free Access to the Your Account App
- Launch the Your Account App
- Assign an Approver to Complete a Self-Service Quote with DocuSign
- Manage Your Contracts with the Your Account App
- Manage Renewals
- View and Download Invoices
- Get Support with the Your Account App
- Turn Off the Your Account App
- Manage Your Quotes with the Your Account App
- Access Your Completed Quotes with the Your Account App
- Update Billing Contact Access to the Your Account App
- User Management Administration
- Enable User Self-Deactivation
- Personal User Information Policies and Timelines
- Manage Personal User Information Visibility for External Users
- Personal User Information Considerations
- Let Users Scramble Their User Data
- Enable Contactless Users
- Enable Enhanced Profile List Views
- Enable Enhanced Permission Set Component Views
- Enable the Enhanced Profile User Interface
- Limit Profile Details to Required Users
- Restrict Permissions Cloning in Profiles
- Enable the Email Domain Allowlist
- Enable Field-Level Security for Permission Sets during Field Creation
- Enable User Access Policies (Beta)
- Administrators and Separation of Duties
- Guidelines for Adding Users
- Add a Single User
- Add Multiple Users
- Considerations for Editing Users
- Unlock Users
- Deactivate Users
- Considerations for Deactivating Users
- Mass Transfer Records
- Freeze or Unfreeze User Accounts
- Create Contactless Users
- Upgrade a Contactless User to a Community License
- Downgrade Experience Cloud Site Users with Community Licenses to...
- Restrict User Email Domains
- User Fields
- View Your Organization’s User Licenses
- See User License Assignments with a Custom Report Type
- When to Use an Internal or External License
- External Identity License Details
- Chatter User Licenses
- Experience Cloud User Licenses
- Channel Account Licenses
- Lightning Platform Starter and Lightning Platform Plus Details
- Database.com User Licenses
- Service Cloud Portal User Licenses
- Sites and Site.com User Licenses
- Authenticated Website User Licenses
- Partner Portal User Licenses
- Customer Portal User Licenses
- Customer Portal—Enterprise Administration User Licenses
- View and Manage Your Permission Set Licenses
- Create a Permission Set Associated with a Permission Set License
- Assign a Permission Set License to a User
- Remove a Permission Set License from a User
- View Your Organization’s Feature Licenses
- Enable a Feature License for a User
- Available Feature Licenses
- View Your Salesforce Org’s Usage-Based Entitlements
- Usage-Based Entitlement Fields
- Delegate Administrative Duties
- Define Delegate Administrators
- Enable Tags
- Adding Tags to the Sidebar
- Delete Personal Tags for Deactivated Users
- Control Who Sees What
- User Permissions
- “View All” and “Modify All” Permissions Overview
- Comparing Security Models
- Verify Access for a Particular Field
- Modify Field Access Settings
- Revoke Permissions and Access
- Create a Connected App for the Tooling API
- Create an Authentication Provider for the Tooling API
- Update the Callback URL in the Connected App
- Create a Named Credential for the Tooling API
- Create a Permission Set to Use the Named Credential
- Download the User Access and Permissions Assistant Package
- Assign the Helper App Access Permission Set
- Create a Permission Set with Required Permissions for the User...
- Set User Authentication for the Tooling API Credential
- Analyze User Permissions
- Analyze Object Permissions
- Analyze Permission Set Groups
- Convert a Profile to a Permission Set
- Report on Permission Assignments by User
- Assign or Unassign Permission Set Groups
- Create a Permission Set Group with the User Access and Permissions...
- Modify a Permission Set Group with the User Access and Permissions...
- Mute Permissions in a Permission Set Group
- Add or Remove Permission Sets from a Permission Set Group
- User Access and Permissions Assistant Considerations
- Manually Grant or Revoke Access with a User Access Policy (Beta)
- Automatically Grant or Revoke Access with a User Access Policy (Beta)
- User Access Policy Considerations (Beta)
- Standard Profiles
- Create and Edit Profile List Views
- Edit Multiple Profiles with Profile List Views
- Create or Clone Profiles
- View a Profile's Assigned Users
- View and Edit Assigned Apps in Profiles
- Assign Record Types and Page Layouts in Profiles
- View and Edit Login Hours in Profiles
- Restrict Login IP Addresses in Profiles
- Password Policy Fields in Profiles
- Edit Session Settings in Profiles
- App and System Settings in the Enhanced Profile User Interface
- Edit Object Permissions in Profiles
- Enable Custom Permissions in Profiles
- Set Field-Level Security for a Field on All Profiles
- Search in the Enhanced Profile User Interface
- Guidelines for Creating Permission Sets and Permission Set Groups
- Create Permission Sets
- Enable Object Permissions in Permission Sets
- Enable User Permissions in Permission Sets
- Set Field Permissions in Permission Sets and Profiles
- Set Field-Level Security for a Field on All Permission Sets
- Enable Custom Permissions in Permission Sets
- Tab Settings
- Set Visualforce Page Access in Permission Sets
- App and System Settings in Permission Sets
- How Is Record Type Access Specified?
- View and Edit Assigned Apps in Permission Sets
- Manage Permission Set Assignments
- Types of Permission Sets
- Permission Set Considerations
- Standard Permission Sets
- Integration Permission Sets
- Create a Flow That Can Activate or Deactivate a Session-Based...
- View Permissions Enabled in a Permission Set or Permission Set Group...
- See the Count of Permission Set Groups a Permission Set Is Added To
- Work with Permission Set Lists
- Search Permission Sets
- Report on Custom Permission Set and Permission Set Group Assignments
- Add Permission Sets to a Permission Set Group
- Remove Permission Sets from a Permission Set Group
- Assign Permission Set Groups to Users
- Mute a Permission in a Permission Set Group
- Permission Set Group Muting Dependencies
- Permission Set Group Status and Recalculation
- Permission Set Groups from Managed Packages
- Permission Set Groups Considerations
- Create Session-Based Permission Set Groups
- Allow Users to Activate or Deactivate a Session-Based Permission Set...
- Permission Set Groups and Combined Permissions View
- Permission Set Group FAQs
- Permission Assignment Expiration Considerations
- Public Group Considerations
- Group Member Types
- Create and Edit Public Groups
- View Group Lists
- Create a Custom Report Type for Public Group Members
- Report on Public Group Membership
- Sharing Records with Manager Groups
- Create and Edit Personal Groups
- Manage Sharing Settings
- Who Has Access to Account Records?
- Considerations for Making Sharing Updates
- Set Your Internal Organization-Wide Sharing Defaults
- Set Your External Organization-Wide Sharing Defaults
- Default Organization-Wide Access Levels
- Organization-Wide Default Access Settings
- Create a User Role
- Assign Users to Roles
- View and Edit Roles
- Guidelines for Success with Roles
- Role Fields
- Role and Territory Sharing Groups
- Managers in the Role Hierarchy
- Sharing Rule Types
- Create Owner-Based Sharing Rules
- Create Criteria-Based Sharing Rules
- Create Guest User Sharing Rules
- Create Sharing Rules Based on Group Membership
- Sharing Rule Categories
- Edit Sharing Rules
- Sharing Rule Considerations
- Defer Sharing Rule Calculations
- Defer Group Membership Calculations
- Automatic Recalculation of Org-Wide Defaults and Sharing Rules
- Asynchronous Deletion of Obsolete Shares
- Manual Sharing in Lightning Experience
- Manual Sharing in Salesforce Classic
- Manual Sharing Considerations
- Viewing Which Users Have Access to Your Records in Salesforce Classic
- Viewing Which Users Have Access to Your Records in Lightning...
- See Account Access from Manual Shares or Account Teams with Reports
- Set the Org-Wide Sharing Defaults for User Records
- Understanding User Sharing
- Report Types Support for User Sharing
- Differences Between User Sharing with Manual Sharing and Sharing Sets
- Control Manual Sharing for User Records
- Control Standard Report Visibility
- Require Permission to View Record Names in Lookup Fields
- View Sharing Overrides
- Built-in Sharing Behavior
- Object-Specific Share Locks
- Create and Edit Folders
- Moving Documents and Email Templates in Folders
- Resolving Insufficient Privileges Errors
- Resolve Permission and Object-Level Access Errors
- Resolve Record-Level Access Errors
- Resolve Process-Level Access Errors
- Create a Restriction Rule
- Restriction Rule Considerations
- Restriction Rule Example Scenarios
- Create a Flow That Applies a Scoping Rule
- Scoping Rule Considerations
- Scoping Rule Example Scenarios
- Records Import Numbers and Types
- What Is Imported for Business Accounts and Contacts?
- What Is Imported for Person Accounts?
- What Is Imported for Leads?
- What’s Imported for Campaign Members?
- What Is Imported for Custom Objects?
- What Is Imported for Solutions?
- Notes on Importing Data
- Rules for Importing Multiple Currencies
- Export Contact Data from ACT!
- Exporting from LinkedIn®
- Export from Outlook
- Export from Other Data Sources
- Export from Salesforce
- Default Field Mapping for ACT!
- Default Field Mapping for Outlook
- Field Mapping for Other Data Sources and Organization Import
- Field Mapping for Importing Leads
- Import Data with the Data Import Wizard
- Add Person Accounts with the Data Import Wizard
- Data Loader
- Undoing an Import
- Import Limits
- Who can use the Data Import Wizard?
- What permissions do I need to import records?
- Why can’t I log into Data Loader?
- Who can import campaign members?
- Can I mass upload data into Salesforce?
- Should I sync Outlook or use import wizards to upload my data into...
- Which data can I import?
- How large can my import file be?
- How do I perform mass updates to records?
- What file formats can the import wizards handle?
- Why is there a delay in importing my file?
- Can I do simultaneous imports?
- How long does it take to complete an import?
- How many records can I import?
- What kind of objects can I import?
- Can I import into custom fields?
- Can I import into fields that are not on my page layout?
- Can I import data into a picklist field if the values don’t match?
- Can I delete my imported data if I make a mistake?
- How do I use the Data Import Wizard to update records that match...
- Where Does Data Import Wizard Obtain the Country for the Country...
- How do I update fields with blank values?
- Can I bulk-assign records to a record type?
- How many campaign members can I import?
- What status is assigned to campaign members?
- Can I import using external IDs?
- Can I match lookups and master-detail records using external IDs?
- Why doesn’t Data Loader import special characters?
- Why do date fields import incorrectly when I use the Data Loader?
- Can I import amounts in different currencies?
- Can I import data in more than one language?
- Can Customer Support help me import my data?
- Delete Multiple Records and Reports
- Notes on Using Mass Delete
- Mass Update Addresses
- Tips for Mass Updating Addresses
- How scalable is Salesforce?
- Do I see a degradation in performance as Salesforce's subscriber...
- Back Up Metadata to Protect and Restore Your Customizations
- Install the Salesforce Backup Managed Package
- Assign the Salesforce Backup License and Permission Set
- Configure Salesforce Backup Settings
- Plan Your Salesforce Backup Strategy
- Add Objects and Records to Your Backup Policy
- Add Files and Attachments to Your Backup Policy
- Set a Custom Backup Schedule
- Run Delta Backups
- Restore Records with Salesforce Backup
- Export Object Data and Related Records from a Backup
- Export File and Attachment Backups
- View and Interpret Salesforce Backup Logs
- Troubleshoot Salesforce Backup
- Salesforce Backup Considerations
- Request a Platform Cache Trial
- Request Additional Platform Cache
- Set Up a Platform Cache Partition with Provider Free Capacity
- Brand Your Salesforce Org’s Domains
- What Is My Domain?
- My Domain Considerations
- My Domain Provisioning and Deployment
- Why Enhanced Domains
- Enhanced Domains Timeline
- Considerations for Enhanced Domains
- Determine Whether Enhanced Domains Are Enabled
- Enable Enhanced Domains
- Troubleshoot Common Errors Related to Enhanced Domains
- Enable Partitioned Domains
- Partitioned Domains for Demo Orgs
- Partitioned Domains for Developer Edition Orgs
- Partitioned Domains for Patch Orgs
- Partitioned Domains for Sandboxes
- Partitioned Domains for Scratch Orgs
- Partitioned Domains for Trailhead Playgrounds
- Understand the My Domain Change Process
- Review Recommended Practices for a My Domain Change
- Prepare for and Schedule a My Domain Change
- Notify Users and Customers About a My Domain Change
- Example My Domain Change Project Checklist
- Example My Domain Change Pre-Deployment Checklist
- Example My Domain Change Post-Deployment Checklist
- Change Your My Domain Details
- Preserve Login Access During a My Domain Login URL Change
- Deploy My Domain Changes
- Determine the Required Authentication Updates After a My Domain Change
- Update Named Credentials After a My Domain Change
- Update Your SAML SSO IdP Configuration After a Login or Site URL...
- Update Your Auth Provider or OpenID Connect IdP Configuration After...
- Update Service Provider Endpoints After a Login or Site URL Change
- Update Your Org for My Domain Changes
- Test My Domain Changes
- Understand Redirections for Previous My Domain Hostnames
- Manage My Domain Redirections
- Prepare for the End of Redirections for Non-Enhanced Domains
- Disable or Remove Your Previous My Domain
- Disable Redirections for Your Previous Force.com Site URLs
- Log My Domain Hostname Redirections
- Set the My Domain Login Policy
- Customize Your My Domain Login Page with Your Brand
- Create an Interview-Based Login Page with My Domain Login Discovery
- Add Identity Providers to the My Domain Login Page
- Customize Your My Domain Login Page for Mobile Auth Methods
- What Is Salesforce Edge Network?
- Considerations for Salesforce Edge Network
- Route My Domain Through Salesforce Edge Network
- Get Your Org Status and Upcoming Maintenance Dates with My Domain
- Link to Salesforce Domains in Packages
- Log In to Salesforce with Code
- What Determines Your URL Formats
- My Domain Hostnames
- My Domain Login and Application URL Formats with Enhanced Domains
- My Domain Login and Application URL Formats Without Enhanced Domains
- My Domain URL Format Changes When You Enable Enhanced Domains
- Phishing and Malware
- Security Infrastructure
- How Is the Health Check Score Calculated?
- Create a Custom Baseline for Health Check
- Custom Baseline File Requirements
- Salesforce Shield
- Security Center Definitions
- Enable Security Center Permissions
- Designate a Parent Tenant in Security Center
- Security Center Dashboards
- Review Detailed Metric Data
- Review Health Check Data
- Update Metric Data
- Review Threat Detection Events
- Use Cases for Alerts
- Define and Deploy Security Policies
- Disconnect a Child Tenant from a Parent Tenant
- Security Center Metrics
- Einstein Data Detect Glossary
- Install and Configure the Einstein Data Detect Managed Package
- Create a Data Detect Policy
- Scan for Patterns with Einstein Data Detect
- View and Classify Results with Einstein Data Detect
- Review Einstein Data Detect Scan Logs
- Which Standard Fields Can I Encrypt?
- Which Custom Fields Can I Encrypt?
- Which Files Are Encrypted?
- What Other Data Elements Can I Encrypt?
- Terminology
- Classic vs Platform Encryption
- Shield Encryption Flow
- Search Index Encryption Flow
- Why Bring Your Own Key?
- Masked Data
- Shield Platform Encryption in Hyperforce
- Required Permissions
- Generate a Tenant Secret with Salesforce
- Manage Tenant Secrets by Type
- Encrypt New Data in Standard Fields
- Encrypt New Data in Custom Fields in Salesforce Classic
- Encrypt New Data in Custom Fields in Lightning Experience
- Encrypt Custom Fields in Installed Managed Packages
- Encrypt Files
- Encrypt Data in Chatter
- Encrypt Search Index Files
- Encrypt CRM Analytics Data
- Encrypt Event Bus Data
- Fix Blockers
- Stop Encryption
- How Deterministic Encryption Supports Filtering
- Encrypt Data with the Deterministic Encryption Scheme
- Work with Key Material
- Rotate Keys
- Back Up Your Tenant Secrets
- Gather Encryption Statistics
- Interpret and Use Encryption Statistics
- Sync Data with Self-Service Background Encryption
- Destroy a Key
- Require Multi-Factor Authentication for Key Management
- Bring Your Own Key Overview
- Generate a BYOK-Compatible Certificate
- Generate and Wrap BYOK Key Material
- Sample Script for Generating a BYOK Tenant Secret
- Upload Your BYOK Tenant Secret
- Opt Out of Key Derivation with BYOK
- Take Good Care of Your BYOK Keys
- Troubleshooting Bring Your Own Key
- How Cache-Only Keys Works
- Prerequisites and Terminology for Cache-Only Keys
- Create and Assemble Your Key Material
- Configure Your Cache-Only Key Callout Connection
- Add Replay Detection for Cache-Only Keys
- Check Your Cache-Only Key Connection
- Destroy a Cache-Only Key
- Reactivate a Cache-Only Key
- Considerations for Cache-Only Keys
- Troubleshoot Cache-Only Keys
- Apply Encryption to Fields Used in Matching Rules
- Retrieve Encrypted Data with Formulas
- Encryption Best Practices
- General Trade-Offs
- Considerations for Using Deterministic Encryption
- Lightning Trade-Offs
- Field Limits
- App Trade-Offs
- Manage Trusted URLs
- Review and Resolve CSP Violations
- Trust Redirections to Your Other Salesforce Orgs
- Manage Redirections to External URLs
- Configure Salesforce CORS Allowlist
- Protect Sensitive Information in Your URLs
- Protect Your Visualforce Pages with Cross-Origin Opener Policy (COOP)
- Restrict Page Resource Requests with Cross-Origin Embedder Policy...
- Enable Clickjack Protection for Visualforce Pages
- Specify Trusted Domains for Inline Frames
- Apply Clickjack Protection to Less Common Browsers
- Modify Session Security Settings
- Enable Browser Security Settings
- Set Trusted IP Ranges for Your Organization
- Control Access to Browser Features
- Require High-Assurance Session Security for Sensitive Operations
- View User Session Information on the Session Management Page
- User Session Types
- Salesforce Platform Cookies
- Using Frontdoor.jsp to Bridge an Existing Session Into Salesforce
- Establish an Inbound Connection with AWS
- Establish an Outbound Connection with AWS
- Considerations for Private Connect with AWS
- Use Activations
- Real-Time Event Monitoring Definitions
- Considerations for Using Real-Time Event Monitoring
- Enable Access to Real-Time Event Monitoring
- Manage Real-Time Event Monitoring Events
- Event Data Streaming
- Event Data Storage
- Using Async SOQL
- Create Logout Event Triggers
- How Chunking Works with ReportEvent and ListViewEvent
- ApiEvent Policies
- ApiAnomalyEventStore Policies
- BulkApiResultEventStore Policies
- CredentialStuffingEventStore Policies
- FileEvent Policies
- ListViewEvent Policies
- LoginEvent Policies
- PermissionSetEventStore Policies
- ReportEvent Policies
- ReportAnomalyEventStore Policies
- SessionHijackingEventStore Policies
- Enhanced Transaction Security Actions and Notifications
- Condition Builder Examples
- Implementation Apex Examples
- Asynchronous Apex Example
- Apex Testing
- Best Practices for Writing and Maintaining Enhanced Transaction...
- Enhanced Transaction Security Metering
- Exempt Users from Transaction Security Policies
- Test and Troubleshoot Your New Enhanced Policy
- Features of the Browser Fingerprint
- Investigate Session Hijacking
- Investigate Credential Stuffing
- Training and Inference Steps
- Investigate Report Anomalies
- Best Practices for Investigating Report Anomalies
- Detection Event Isn’t Anomalous
- Detection Event Possibly Anomalous
- Detection Event Is Definitely Anomalous but Maybe Not Malicious
- Detection Event Is Confirmed Malicious
- Investigate API Request Anomalies
- Best Practices for Investigating API Request Anomalies
- API Detection Event Isn’t Anomalous
- API Detection Event Possibly Anomalous
- API Detection Event Is an Anomaly but Isn’t Clearly Malicious
- API Detection Event Is Confirmed Malicious
- Investigate Guest User Anomalies
- Best Practices for Investigating Guest User Anomalies
- Make the Threat Detection App Visible to Users
- View Events and Provide Feedback
- Explore Event Log File Data using the Event Log File Browser (Beta)
- Configure Remote Site Settings
- Create and Edit an OAuth External Credential with the Browser Flow
- Create and Edit an OAuth External Credential with the JWT Bearer Flow
- Create and Edit an OAuth External Credential with the Client...
- Create and Edit an AWS Signature v4 External Credential
- Create and Edit a Custom Authentication External Credential
- Create and Edit a No Authentication External Credential
- Create and Edit a JWT External Credential
- Create and Edit a Basic Authentication External Credential
- Additional Tasks for External Credentials
- Enable External Credential Principals
- Enable User External Credentials
- Permission Concepts for User External Credentials
- Create and Edit Custom Headers
- Use API Keys with Named Credentials
- Using Basic Authentication with Named Credentials
- Named Credential Formula Functions
- Create and Edit a Named Credential
- Define a Legacy Named Credential
- Grant Access to Authentication Settings for Legacy Named Credentials
- Authentication Protocols for Named Credentials
- Set Up JWT Claims for Named Credentials
- Considerations for Named Credentials
- Generate a Self-Signed Certificate
- Generate a Certificate Signed by a Certificate Authority
- Set Up a Mutual Authentication Certificate
- Configure Your API Client to Use Mutual Authentication
- Manage Master Encryption Keys
- Replace the Default Proxy Certificate for SAML Single Sign-On
- Technical Requirements for Phones
- Performance Assistant
- What Is EPT?
- Plan Your Performance Test and Identify Key Personas
- Set Up and Run Performance Tests
- Network Best Practices
- Device and Browser Best Practices
- Org Configuration Best Practices
- Improve Virtual Desktop Environment Performance
- System Overview: Schema
- System Overview: API Usage
- System Overview: Business Logic
- System Overview: User Interface
- System Overview: Most Used Licenses
- System Overview: Portal Roles
- Data and Storage Resources
- Get Adoption and Security Insights for Your Organization
- Considerations for Using Login Forensics
- Enable Login Forensics
- Monitor Training History
- Monitor Setup Changes with Setup Audit Trail
- Track Field History for Standard Objects
- Track Field History for Custom Objects
- Disable Field History Tracking
- Set Up Debug Logging
- View Debug Logs
- Collect Debug Logs for Guest Users
- Monitoring Scheduled Jobs
- Monitor Background Jobs
- Monitor Bulk Data Load Jobs
- View Bulk Data Load Job Details
- Install a Package
- Configuring Installed Packages
- Uninstall a Managed Package
- View Installed Package Details
- Importing Package Data
- Namespace Permission Set Licenses in Packages
- Assign Licenses for Installed Packages
- Removing Licenses for Installed Packages
- Responding to License Manager Requests
- Assigning Licenses Using the API
- Package Usage
- Upgrading Packages
- Can I uninstall packages that I installed from AppExchange?
- Who Can Use AppExchange?
- Why did my installation or upgrade fail?
- Can I customize AppExchange packages?
- Who can use AppExchange packages?
- How can I upgrade an installed package?
- How secure are the components I install?
- What happens to my namespace prefix when I install a package?
- Can I reinstall an AppExchange package after uninstalling it?
- When I install a package that’s listed on AppExchange, do custom...
- Do AppExchange managed packages count against data storage limits?
- Learn More About Setting Up Salesforce
Assign Custom Record Types in Permission Sets
You can assign record types to users in permission sets.
Required Editions and User Permissions
- From Setup, in the Quick Find box, enter Permission Sets , and then select Permission Sets .
- Select a permission set, or create one.
- On the permission set overview page, click Object Settings , then click the object you want.
- Click Edit .
- Select the record types you want to assign to this permission set.
- Click Save .
- How Is Record Type Access Specified? Assign record types to users in their profiles or permission sets (or permission set groups), or a combination of these. Record type assignment behaves differently in profiles and permission sets.

Cookie Consent Manager
General information, required cookies, functional cookies, advertising cookies.
We use three kinds of cookies on our websites: required, functional, and advertising. You can choose whether functional and advertising cookies apply. Click on the different cookie categories to find out more about each category and to change the default settings. Privacy Statement
Required cookies are necessary for basic website functionality. Some examples include: session cookies needed to transmit the website, authentication cookies, and security cookies.
Functional cookies enhance functions, performance, and services on the website. Some examples include: cookies used to analyze site traffic, cookies used for market research, and cookies used to display advertising that is not directed to a particular individual.
Advertising cookies track activity across websites in order to understand a viewer’s interests, and direct them specific marketing. Some examples include: cookies used for remarketing, or interest-based advertising.
Cookie List
Grow your business with Salesforce Starter
Deepen customer relationships with sales, service, and marketing in one app.
About 15 mins
Learning Objectives
Record-level security, org-wide sharing, set your org-wide sharing defaults, tell me more....
- Challenge +500 points
Control Access to Records
After completing this unit, you'll be able to:
- List the four ways to control access to records.
- Describe situations in which to use each of the four record-level security controls.
- Explain how the different record controls interact with each other.
- Set org-wide sharing defaults to control access to records.
To control data access precisely, you can allow particular users to view specific fields in a specific object, but then restrict the individual records they're allowed to see.
Record access determines which individual records users can view and edit in each object they have access to in their profile. First ask yourself these questions:
- Should your users have open access to every record, or just a subset?
- If it’s a subset, what rules should determine whether the user can access them?
For our example Recruiter app, let’s say you create a new profile called Recruiter to give recruiters the object-level permissions they need. You restrict the power to delete recruiting-related objects, so recruiters will never be able to delete these objects. However, granting recruiters permission to create, read, or edit recruiting objects does not necessarily mean recruiters can read or edit every record in the recruiting object. This is a consequence of two important concepts:
- The permissions on a record are always evaluated according to a combination of object-level, field-level, and record-level permissions.
- When object-level permissions conflict with record-level permissions, the most restrictive settings win.
That means even if you grant a profile create, read, and edit permissions on the recruiting objects, if the record-level permissions for an individual recruiting record are more restrictive, those are the rules that define what a recruiter can access. However, as you'll see, record-level permissions offer layers of increasing access, so it's important to know which record-level permissions are observed to understand the level of access a user has.
You control record-level access in four ways. They’re listed in order of increasing access. You use org-wide defaults to lock down your data to the most restrictive level, and then use the other record-level security tools to grant access to selected users, as required.
- Org-wide defaults specify the default level of access users have to each other’s records.
- Role hierarchies ensure managers have access to the same records as their subordinates. Each role in the hierarchy represents a level of data access that a user or group of users needs.
- Sharing rules are automatic exceptions to org-wide defaults for particular groups of users, to give them access to records they don’t own or can’t normally see.
- Manual sharing lets record owners give read and edit permissions to users who might not have access to the record any other way.
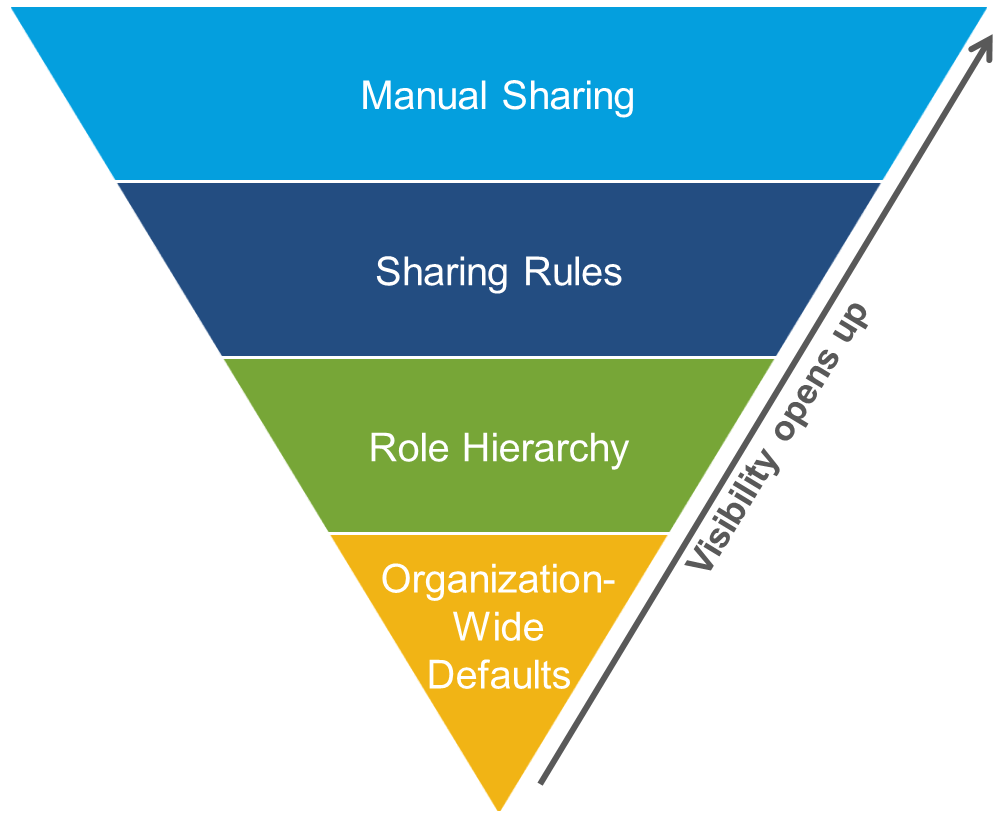
The visibility and access for any type of data is determined by the interaction of the above security controls, based on these key principles.
- A user’s baseline permissions on any object are determined by their profile.
- If the user has any permission sets assigned, these also set the baseline permissions in conjunction with the profile.
- Access to records a user does not own are set first by the org-wide defaults.
- If the org-wide defaults are anything less than Public Read/Write , you can open access back up for certain roles using the role hierarchy.
- You can use sharing rules to expand access to additional groups of users.
- Each record owner can manually share individual records with other users by using the Share button on the record.
You’ve already seen how to configure object-level and field-level access using profiles and permission sets. Now we’ll look at details of the various record-level security controls.
Org-wide defaults specify the baseline level of access that the most restricted user should have. Use org-wide defaults to lock down your data, and then use the other record-level security and sharing tools (role hierarchies, sharing rules, and manual sharing) to open up the data to users who need it.
Object permissions determine the baseline level of access for all the records in an object. Org-wide defaults modify those permissions for records a user doesn't own. Org-wide sharing settings can be set separately for each type of object.
Org-wide defaults can never grant users more access than they have through their object permission.
To determine the org-wide defaults you need for your app, ask yourself these questions about each object:
Who is the most restricted user of this object?
Is there ever going to be an instance of this object that this user shouldn't be allowed to see?
Is there ever going to be an instance of this object that this user shouldn't be allowed to edit?
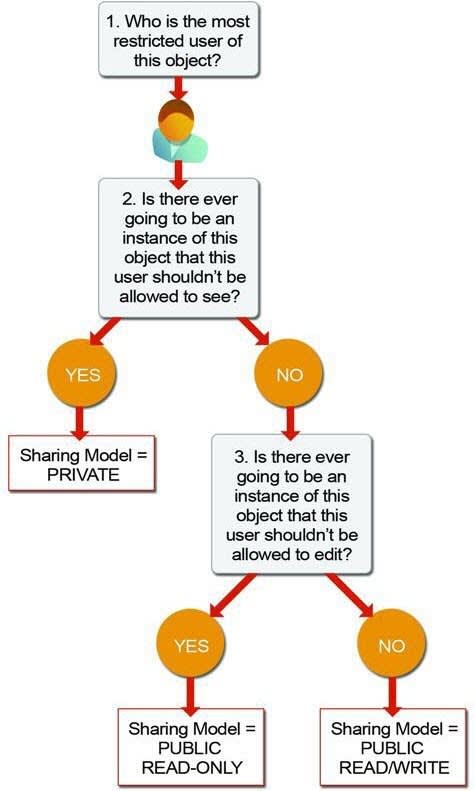
Based on your answers, you can set the sharing model for that object to one of these settings.
Only the record owner, and users above that role in the hierarchy, can view, edit, and report on those records.
Public Read Only
All users can view and report on records, but only the owner, and users above that role in the hierarchy, can edit them.
Public Read/Write
All users can view, edit, and report on all records.
Controlled by Parent
A user can view, edit, or delete a record if she can perform that same action on the object it belongs to.
When the org-wide sharing setting for an object is Private or Public Read Only , an admin can grant users additional access to records by setting up a role hierarchy or defining sharing rules. Sharing rules can only be used to grant additional access. They cannot be used to restrict access to records beyond what was originally specified with the org-wide sharing defaults.
As an example, let’s go through and answer the above list of questions for the Position object in the Recruiting app.
A member of the Standard Employee profile. All that they're allowed to do is view a position.
No. Although the values for the minimum and maximum pay fields are hidden from standard employees, they're still allowed to view all position records.
Yes. Standard employees aren’t allowed to edit any position record.
Since we answered “Yes” to the third question, the sharing model for the Position object should be set to Public Read Only. By repeating the same exercise with the other recruiting objects, you can easily figure out the appropriate org-wide default settings for them. The Standard Employee profile is the most restricted user for each object, and there are going to be candidate, job application, and review records that particular employees won't be able to view. Consequently, the sharing model for the Candidate, Job Application, and Review objects should all be set to Private .
You can't set the org-wide defaults for the Review object, because that object is on the detail side of a master-detail relationship, and a detail record automatically inherits the sharing setting of its parent. So in our app, the Review object is automatically set to Private .
Use org-wide defaults to specify the baseline level of access that the most restricted user should have.
- From Setup, in the Quick Find box, enter Sharing Settings , and then select Sharing Settings .
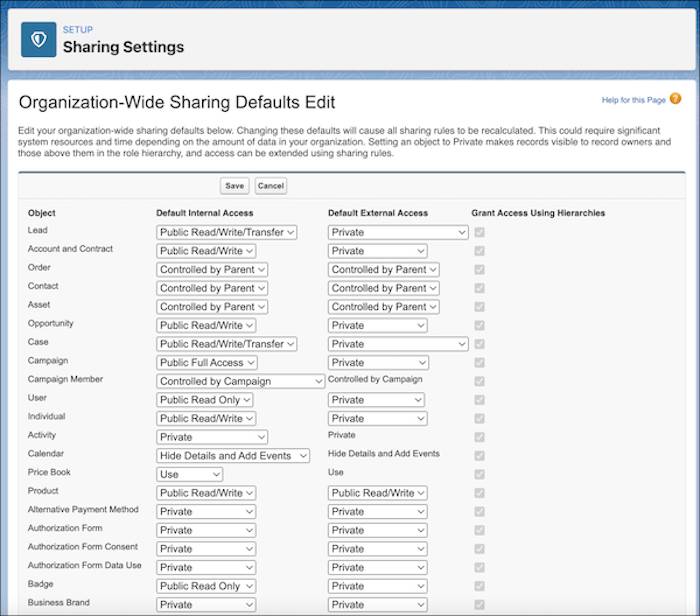
- For each object, select the default internal access and default external access.
- To disable automatic access using your hierarchies, deselect Grant Access Using Hierarchies for any custom object that doesn't have a default access of Controlled by Parent.
By default, a role hierarchy automatically grants access to records for users above the record owner in the hierarchy. Setting an object to Private makes those records visible only to record owners and those above them in the role hierarchy. Use the Grant Access Using Hierarchies checkbox to disable access to records to users above the record owner in the hierarchy for custom objects. If you deselect this checkbox for a custom object, only the record owner and users granted access by the org-wide defaults receive access to the records.
Even if Grant Access Using Hierarchies is deselected, some users—such as those with the “View All” and “Modify All” object permissions and the “View All Data” and “Modify All Data” system permissions—can still access records they don’t own.
Updating the org-wide defaults automatically runs sharing recalculation to apply any access changes to your records. You receive a notification email when the recalculation completes and you can refresh the Sharing Settings page to see your changes. To view the update status, from Setup, in the Quick Find box, enter View Setup Audit Trail , and then select View Setup Audit Trail .
Once you’ve locked down your data with org-wide defaults, the resulting settings might be too restrictive for some users. You can then use the remaining record-level security controls (role hierarchies, sharing rules, and manual sharing) to open up record access selectively to specific employees who need it.
Apex managed sharing allows developers to programmatically share records associated with custom objects. When you use Apex managed sharing for any custom object, only users with the “Modify All Data” permission can add or change the sharing on that custom object's records, and the sharing access stays the same even if the record owner changes. For more information, see Apex Sharing .
- Sharing Settings
- Sharing Considerations
- Organization-Wide Sharing Defaults
- Security Implementation Guide
- Get personalized recommendations for your career goals
- Practice your skills with hands-on challenges and quizzes
- Track and share your progress with employers
- Connect to mentorship and career opportunities
SimplySfdc.com
Saturday, november 18, 2017, enable record type with permission set.

No comments:
Post a comment, page-level ad.
- App Building
- Be Release Ready – Summer ’24
- Integration
- Salesforce Well-Architected ↗
- See all products ↗
- Career Resources
- Essential Habits
- Salesforce Admin Skills Kit
- Salesforce Admin Enablement Kit
Home » Video » Automate This! — Automatically Assign and Remove a Permission Set

Automate This! — Automatically Assign and Remove a Permission Set
Welcome to “Automate This!” In this new, live-streamed video series, we cover all things automation, from use cases and best practices to showcasing solutions built by #AwesomeAdmin Trailblazers like you. Automation allows you to remove manual tasks, drive efficiency, and eliminate friction and redundancy. With the recent announcement of the future retirement of Workflow Rules and Process Builder , we’ll focus heavily on record-triggered flow solutions this year. Watch how I use the power of Flow to assign and remove a permission set from a user, and then read all the details in the post below.
Stay tuned for next month’s Automate This! Live .
When you think about automation, the use cases that come to mind are most likely automation that your customers or users can benefit from. But did you know that you can automate user management tasks to make your life as an admin easier? Let’s #WorkSmartNotHard by automating routine, repetitive tasks for ourselves so we have more time to focus on value-added tasks, like delivering new enhancements to our users!
As an admin, it’s important to be security-minded, ensuring your org is secure and your users have least privilege access. Use our Security & Visibility Admin Configuration Kit to guide you toward a recommended solution for object-level security, field-level security, and record access.
Gone are the days you need Post-It notes to remind you to manually add and remove users from permission sets. Now, you can configure Salesforce to remember for you. With Flow, you can automatically assign and remove permission sets to/from a user as long as certain conditions are met.
Understand the object relationship
First things first. Let’s understand the relationship between user and permission sets.
User and Permission Sets are objects. The User object holds all the records of your users. The Permission Set object holds all the permission sets in your org. Then, you have the Permission Set Assignment object, which is the junction object that holds the record that ties the user to a specific permission set. A permission set assignment record has two important attributes:
- AssignedId: This is the user ID.
- PermissionSetId: This is the permission set ID.

A user can have none or many permission sets, which would be reflected in the Permission Set Assignment object.
Let’s review the overall process in Salesforce
Before we log in to Salesforce and create a new flow, the first step in creating automation is to understand the overall process. There are two parts to this process: adding a user to a permission set and removing a user from a permission set.
First, let’s review the steps to manually assign a permission set to a user.
- Search for the user.
- View the user’s record.
- Navigate to the user’s Permission Set Assignments list.
- Click Edit Assignments .
- Select the permission set from the Available Permission Sets list to add to the Enabled Permission Sets list.
- Click Save .
![salesforce permission set record type assignment Adding and removing permission sets to/from a user]](https://d3nqfz2gm66yqg.cloudfront.net/images/20220308164039/image-7-1024x558.png)
Note: You can assign a permission set in the user interface (UI) only if it’s listed in the Available Permission Sets list.
Let’s now review the steps to manually remove a permission set from a user.
- Navigate (hover over) to the user’s Permission Set Assignments list.
- Locate the permission set you want to remove and click the Del link.

Note: You can only delete a permission set in the UI if it’s already enabled for the user.
Your automation (aka flow) needs to accommodate for these UI restrictions or else your flow will fail.
- Before you assign a permission set, you need to ensure the user isn’t already assigned to the permission set.
- Before you remove a permission set, you need to ensure the user is already assigned to the permission set.

Let’s document the process
Before building automation in Flow Builder, I’ve found it helpful to think out the steps logically before getting my hands on the keyboard. This is especially true if you’re just learning Flow or when working on a highly complex process. It’s easier to make changes on paper than to have to refactor your configuration.
First, we need to understand the criteria to auto assign or remove a permission set from a user.
For our business requirements, when a new Finance user is added to Salesforce, the ABC permission set will be assigned. If an existing user leaves the Finance department and moves to the Sales Division, then the ABC permission set will be removed from the user.
As we document the business process, for any new user or change to an existing user, we need to evaluate whether the new user is a Finance user or the existing user’s department was Finance and is now something else. Then, if it is a new Finance user, we’ll assign a permission set. If the user was formerly part of the Finance department, we’ll remove the permission set.
Let’s take a closer look at the documented steps for assigning a new permission set.
First, we need to identify the permission set. We know it by name, but Flow needs to know the permission set ID. We get the ID by looking at the details of the permission set record. Here, we’ll follow best practice and find the permission set record by its API or developer name, as this is less likely to change than the permission set name/label.
But let’s say you can’t find the permission set by that name. Perhaps you were given the wrong name. Essentially, without that permission set record, your business process ends. You can’t do much else at that point.
When working with Flow, you need to put those safety verifications or guardrails in place to prevent your flow from failing. Visually, in Salesforce Setup, you’d be able to see in the UI whether the user is already assigned to the permission set. Essentially, behind the scenes, your flow will look to see if there’s a permission set assignment record for the user and the permission set.
If the user doesn’t have the permission set, then the next step is to assign the permission set to the user (or create the permission set assignment record). However, if the user already has the permission set, no further action is needed. Your work is done.
When we find records, we’ll use a Get Records Flow element to find information about the permission set. To determine whether the Get Records element found a permission set record, we need to make a decision. Hence, we’ll use a Decision element. Next, to see if the user is assigned to the permission set, we need to query the Permission Set Assignment object, so we’ll once again use the Get Records element. Next, we need to determine whether the Get Records element found a permission set assignment record for that user and permission set, which is done using another Decision element. Lastly, if the permission set assignment record is found, we’ll create a new permission set assignment record for the user permission set combination with a Create Records element.
Now, let’s look at the scenario of removing a permission set.
Again, similar to the process of assigning a permission set, we need to identify the permission set to get the permission set ID. If we can’t find the permission set, our work is done. Again, we need to put those safety verifications in place to prevent our flow from failing. Visually, in Setup, you can see whether the user is assigned to the permission set you wish to remove. Like the first scenario, you’re looking to see if there’s a permission set assignment record for that user and permission set.
If the user has the permission set, the next step is to remove it (or delete the permission set assignment record). If the user doesn’t have the permission set, no action is needed.
When we find records, we’ll use a Get Records element to find information about the permission set. To determine whether the Get Records element found a permission set record, we need to make a decision. So, we’ll use a Decision element. Next, to see if the user is assigned to the permission set, we need to query the Permission Set Assignment object, so we’ll once again use the Get Records element. Next, we need to determine whether the Get Records element found a permission set assignment record for that user and permission set, which is done using another Decision element. Lastly, if the permission set assignment record is found, we’ll remove the permission set assignment record for the user permission set combination with a Delete Records element.
While we can design each process as its own process and its own flow, did you notice what both processes have in common? Yes, there are four common steps between the two processes. So, an even better design would be to consolidate the steps so we don’t build the same steps over and over again.
One more thing before we get into Flow Builder.
We need to determine information we need (or our inputs) so Salesforce can automagically assign permission sets to a user:
- Who is the user?
- What is the permission set?
- What are we looking to do (in this case—assign or remove a permission set)?
These three pieces of information will be stored as text values that are three separate variables.
What’s a variable, you ask? A variable is a container that holds a piece of information for use somewhere later in the flow or to be passed off outside the flow. I think of it as a Tupperware container.

- The variable varUserId will hold the user ID.
- The variable varPermissionSetName will hold the API or developer name of the permission set name.
- The variable varPermissionSetAction will hold the value “Add” or “Remove” which reflects what we want to do with the permission set.
We’ll use the permission set developer name to find the permission set ID because #AwesomeAdmins do not hard code IDs in their automation. If we find the permission set, we’ll store the ID in a variable called varPermissionSetId. Otherwise, the variable will be empty, signifying no permission set.
Another valuable piece of information we’ll get to within the process is whether the user is already assigned to the permission set. We’ll hold this in a variable called varDoesUserHavePermissionSet. If it’s true, we’ll store the assignee ID. Otherwise, the variable will be empty, signifying the user does not have a permission set.
We have a total of five variables that will hold important information we’ll use to make informed decisions or to take action within the flow.

Let’s build our automation!
Now that we have that squared away, let’s look at how to build this in Flow Builder. Did you notice how long it took before we even logged in to Salesforce to configure?! There’s a big thought process that needs to happen before we build.
Our process will be broken into two flows: a record-triggered flow and an autolaunched flow. Our process begins with something that happens to a user record—when a new user is created or an update is made to an existing user record. This translates into a record-triggered flow. Regardless of whether the user is a new Finance user or was previously a Finance user, we didn’t want to create the same process steps to handle the Add or Remove permission set action. This takes us back to the consolidated process design, remember?
We’re going to build that consolidated Assign/Remove permission set process as an autolaunched flow, which means this flow will fire when something else triggers it. In our case, this will be triggered by a record-triggered flow. We’ll re-use the same autolaunched flow twice in our process—for the permission set assignment and permission set removal—and the flow will know what to do based on three input variables our record-triggered flow will pass to the autolaunched flow. When you re-use an autolaunched flow in another flow, it’s called a subflow. We’re essentially building a componentized flow that can be reused anytime there’s a need to assign or remove a permission set from a user. #WorkSmartNotHard. Build it once, maintain it once, and reuse it over and over again.

In order for our record-triggered flow to call or invoke an autolaunched flow, we need to build the autolaunched flow first.

First, select to create an autolaunched flow. Now, you’ll create five text variables.
The first text variable is varUserId. This will store the user ID passed from the record-triggered flow. Make this available for input.
- Resource: Variable
- Name: varUserId
- Data Type: Text
- Available for input: Checked
![salesforce permission set record type assignment The configured varUserId text variable]](https://d3nqfz2gm66yqg.cloudfront.net/images/20220308165240/image-14.png)
The second text variable is varPermissionSetName. This will store the permission set API or developer name passed from the record-triggered flow. Make this available for input.
- Name: varPermissionSetName

The third text variable is varPermissionSetAction. This will store the value of “Add” or “Remove” passed from the record-triggered flow. Make this available for input.
- Name: varPermissionSetAction

The fourth text variable is varPermissionSetId. This will store the permission set ID when we query the Permission Set object using the value in the varPermissionSetName variable.
- Name: varPermissionSetId
![salesforce permission set record type assignment [Image: image.png][Alt text: The configured varPermissionSetId text variable](https://d3nqfz2gm66yqg.cloudfront.net/images/20220308165514/image-17.png)
The last and fifth text variable is varUserHasPermissionSet. This will store the assignee ID when we query the Permission Set Assignment object for the user and permission set and there is a value found.
- Name: varUserHasPermissionSet

Our first Flow element is a Get Records. We’ll use the permission set API or developer name to get the permission set ID. If a record is found, we’ll store the permission set ID in the variable varPermissionSetId. If no record is found, we’ll set the variable to null. This is done by checking the attribute box for “When no records are returned, set specified variables to null.”
- Name: Lookup Permission Set Id
- Object: Permission Set
- Filter: Name Equals varPermissionSetName
- How to Store Record Data: Choose fields and assign variables (advanced)
- Where to Store Field Values: In separate variables
- Select Variables to Store Permission Set Fields: Id → varPermissionSetId
- “When no records are returned, set specified variables to null”: Checked

- Name: Perm Set ID Found
- Outcome: Permission Set ID Found | varPermissionSetId Is Null False
- Default Outcome: No Permission Set ID Found

To see if the user is assigned to the permission set, we need to query the Permission Set Assignment object with another Get Records element to find a record with the user and the permission set. If a permission set assignment record is found, then we’ll take the assignee ID and store it in the variable varUserHasPermissionSet. If no record is found, we’ll set the variable to null by enabling the attribute “When no records are returned, set specified variables to null.”
- Name: Lookup Permission Set Assignment
- Object: Permission Set Assignment
- Filter Permission Set Assignment Records:
- AssigneeId Equals varUserId
- PermissionSetId Equals varPermissionSetId
- Select Variables to Store Permission Set Fields: AssigneeId → varUserHasPermissionSet

In our next step, we need to determine whether the Get Records element found a permission set assignment record for that user and permission set using another Decision element. We have two outcomes: “Add Path - No Permission Set” and “Remove Path - Has Permission Set”.
As discussed earlier, before we can add a permission set to a user, we need to ensure the user does not already have the permission set or else the flow will fail. Here, we check that the varHasPermissionSet variable has a null value (that is, Is Null True) and the varPermissionSetAction is “Add”.
And, in order for a permission set to be removed, the user must be assigned to the permission set. Here, we check that the varHasPermissionSet variable has a value (that is, Is Null False—two negatives equals a positive) and the varPermissionSetAction is “Remove”.
This decision puts the guardrails in place in Flow, where these same guardrails are already in the permission set UI.
- Name: Check Permission Set Assignment
- Outcome #1: Add Path - No Permission Set | varUserHasPermissionSet Is Null True AND varPermissionSetAction Equals Add
- Outcome #2: Remove Path - Has Permission Set | varUserHasPermissionSet Is Null False AND varPermissionSetAction Equals Remove

If the permission set assignment record is found and the varPermissionSetAction is “Add”, then we’ll create a new permission set assignment record for the user permission set combination with a Create Records element, where the AssigneeId field is set to the value in the variable varUserId and the PermissionSetId field is set to the value in the variable varPermissionSetId.
- Name: Add User to the Permission Set
- How Many Records to Create: One
- How to Set the Record Fields: Use separate resources, and literal values
- AssigneeId: varUserId
- PermissionSetId: varPermissionSetId

Lastly, if the decision outcome is to remove a permission set for the user, then we’ll delete the permission set assignment record for the user permission set ID combination using a Delete Records element. We’ll delete the permission set assignment record where the assigneeId equals the variable varUserId and permission set ID equals the variable varPermissionSetId combo matched.
- Name: Remove Permission Set
- How to Find Records to Delete: Specify Conditions
- Filter Permission Set Assignment Records: AssigneeId Equals varUserId AND PermissionSetId Equals varPermissionSetId

Don’t forget to test it using the Flow debugger, and activate the autolaunched flow.
With the modularized flow created, we now need to create our trigger to fire the process of assigning or removing permission sets to/from a user. As mentioned earlier, we’ll use a record-triggered flow to trigger the autolaunched flow.
For our use case, when there’s a new Finance user or a user has left Finance, we want the permission set to either be assigned or removed. The action to be taken with the permission set is done by invoking the autolaunched flow we just created. In the case of the new Finance user, a permission set will be assigned. For the user who is no longer a Finance user, a permission set will be removed.

The record-triggered flow we build will look like this.
![salesforce permission set record type assignment The configured record-triggered flow for assigning or removing a permission set for a new Finance user or a user no longer part of Finance]](https://d3nqfz2gm66yqg.cloudfront.net/images/20220308170155/image-26-1024x1008.png)
The record-triggered flow starts when a user record is created or edited. We don’t have any entry conditions specified, as we want to check for new Finance users or users where the department was Finance but has changed.
- Object: User
- Trigger the Flow When: A record is created or updated
- Department is Changed True
- Department Does Not Equal Finance
- Department Equals Finance
- Optimize the Flow for: Actions and Related Records

Once a user record passes the entry criteria, we have a decision to determine what type of user this is—a new user or an existing user who is no longer part of Finance, and these are reflected in the two outcomes.
To define the new user outcome, we need the record to be new and the department to equal “Finance.”
For the Existing User Previously Finance Department outcome, we need the user ($Record.Id) to be active, the user’s previous department ($Record_Prior> Department) was “Finance,” and the user’s current department ($Record>Department) is changed.
Since this is an after save flow (that is, a record-triggered flow that fires after a record is saved in Salesforce), we need a mechanism to indicate whether a record is new, as we can’t go by the record ID is blank (which is a filter we can use in a before save flow, which fires before the record is saved in Salesforce).
We’ll introduce a new formula resource that will look at whether the record is new and the department is Finance.
- Resource Name: NewFinanceUserFormula
- Resource Type: Formula
- Data Type: Boolean
- Formula: ISNEW() && {!$Record.Department}= "Finance"

Here’s how you configure the Decision element:
- Name: New or Previously a Finance User
- Outcome #1: New Finance User | NewFinanceUserFormula Equals True
- $Record.IsActive Equals True
- $Record_Prior> Department Equals Finance
- $Record>Department is Changed True

For the New Finance User outcome, we’ll add a subflow interaction, which will allow this record-triggered flow to invoke the autolaunched flow. Locate and select the autolaunched flow we created.
Here, we’ll include the three input variables and pass the following information to our subflow:
- varPermissionSetAction: Add (This specifies we want to add a permission set.)
- varPermissionSetName: ABC_Permission_Set (This is the permission set’s API name.)
- varUserid: {!$Record.Id} (We’re using the ID of the user record that triggered the record-triggered flow.)
This will tell the subflow that I want to add the ABC permission set to the user record that triggered the process.

For the Existing User Previously Finance Department outcome, we’ll add another subflow interaction. Locate and select the autolaunched flow we created.
We’ll include the three input variables and pass the following information to our subflow:
- varPermissionSetAction: Remove (This specifies we want to remove a permission set.)
This will tell the subflow that I want to remove the ABC permission set from the user record that triggered the process.

Test both expected outcomes (new Finance user and an existing user who used to belong to Finance) and one where the user does not meet the entry criteria (that is, new user with a department that’s not Finance) using Flow debugger. Lastly, activate the flow.
As additional scenarios come up for automatically assigning or removing a permission set, you can create a new record-triggered flow that invokes the autolaunched flow as subflows.
- Documentation: Salesforce Security Guide - Permission Sets
- Trailhead: Flow Testing and Distribution
- Salesforce Architects: Record-Triggered Automation Decision Guide
Want to see more good stuff? Subscribe to our channel!
Jennifer w. lee.
Jennifer is a Lead Admin Evangelist at Salesforce and the host of our live streamed series Automate This! She is Flownatic, 8x certified Application Architect, Trailhead enthusiast, and Golden Hoodie recipient. Prior to joining Salesforce, Jen was a Koa customer, blogger (Jenwlee.com), founding co-host of Automation Hour, and a Salesforce MVP (2016-2021).
- Jen’s Top Summer ’24 Release Features | Be Release Ready
- Einstein for Formulas | Spring ’24
- Jen’s Top Spring ’24 Release Features
- How to Automatically Deactivate Users Who Haven’t Logged On in 90 Days

Related Posts

Use a Custom Error Element and Flow to Prevent Record Deletion | Automate This!
By Jeff Susich | April 17, 2024
Welcome to another “Automate This!” In this live-streamed video series, we cover all things automation, from use cases and best practices to showcasing solutions built by Awesome Admin Trailblazers like you. With automation, you can remove manual tasks, drive efficiency, and eliminate friction and redundancy. In this episode, let’s see how Jeff Susich uses a […]

Level Up Your Approvals with Flows and the Custom Error Element | Automate This!
By Jon Chen | April 17, 2024
Welcome to another “Automate This!” In this live-streamed video series, we cover all things automation, from use cases and best practices to showcasing solutions built by Awesome Admin Trailblazers like you. With automation, you can remove manual tasks, drive efficiency, and eliminate friction and redundancy. In this episode, learn how Jon Chen designs a solution […]
Use Flows and Experience Cloud to Access Salesforce Scheduler | Automate This!
By Lynn Guyer | March 21, 2024
Welcome to another “Automate This!” In this live-streamed video series, we cover all things automation, from use cases and best practices to showcasing solutions built by Awesome Admin Trailblazers like you. With automation, you can remove manual tasks, drive efficiency, and eliminate friction and redundancy. In this episode, learn how Lynn Guyer requests support from […]

Salesforce Hacker
23 september 2013, master record types with permission sets.

- Only Master [default on profile and no permission sets] - the user will skip the jump screen and the Master (null) record type will automatically be set on the newly created record
- Master defaulted on the profile + only 1 custom record type on a permission set - the user will skip the jump screen and the custom record type will automatically be set on the newly created record
- Master defaulted on the profile + > 1 custom record type on one or more permission sets - the user will get the jump screen every time in order to choose which custom record type they want to assign to the record they are creating
4 comments:

What would be the method for setting a default record type when that profile has access to more than one record type? Basically, it's possible in the personal settings, but those are not easily updateable by the admin (have to log in as each user). In the instance of having two different case types, L1 and L2, you would want the L1 team to have their record type default to the L1 type, but still have the ability to transfer to L2 as well as still see the L2 case. Are they basically stuck having to go through the jump screen?
Hi Patrick, not entirely sure what you're trying to accomplish in this use case. You can have only one default which is the exclusive domain of the profile. Permission sets are only designed to layer non-default record types for a given user. Can you tell me more about your use case? Thanks!
Apologies--I missed this response. We have a team that only ever originates one kind of record type for an object. They are a Level 1 team that is on the phone and need to quickly just click "new" and not have to choose from the dropdown--because 100% of the time they will be choosing Record Type A. They never create records of type B. However, they need to be able to convert Type A into Type B and also still be engaged with that record to close it out. So they need access to both record types at the profile level, but want the default when creating to bypass the jump screen and always be Record Type A. Now, they can set this under My Personal Information-->Record Type Selection (or in the new interface My Settings-->Display & Layout-->Set Default Record Types). They will essentially bypass the jump screen while still having permissions to both record types. However, the only way to do this is to have the users go in and set that setting on their own (or login as each of them and do it for them--with a few hundred users, that won't fly). From what I've seen there's no way to mass set that personal setting, nor is there a corresponding profile or permission set level permission that allows this function.
Hi Patrick, Unfortunately, the default behavior has been that way since a couple years before my time. AFAIK, there's no way to change the behavior in a programmatic fashion.
Note: Only a member of this blog may post a comment.
Using Flow to Assign Permission Set
September 17, 2021 Yumi Ibrahimzade Automation , Flow 19

A permission set can be described as a collection of extra permissions and settings that extends users' existing permissions. Permission sets can be used to give extra permissions to users without modifying their profiles. User can have only one profile but they can have multiple permission sets assigned to them. This way, you can have minimum profiles in the system but give various permissions to specific people.
Permission sets can be assigned only to users. It is not possible to assign a them to a public group, role, or profile. Read this article to learn more about permission sets.
There are two different way to assign a permission set. First one is directly from the user record.
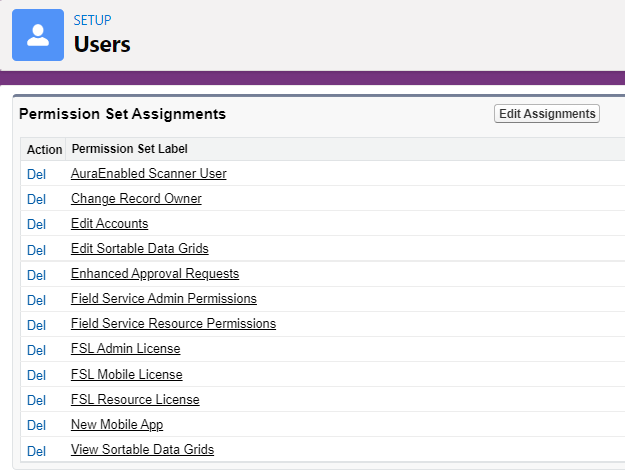
Second way is opening the permission set and clicking on the Manage Assignments button.
You have to go to the setup to perform both of these actions, which means that you need admin permissions.
However, using a flow, it is possible to build a screen that lets the current user select a user and a permission set to assign to him/her. This would be a great admin tool for manual assignments. It is also possible to build a record-triggered flow to automatically assign permission set(s) when a user becomes active. This is a great way to reduce manual work. You can read this post to learn about flow types and their differences.
Building a Screen Flow to Assign Permission Sets
1- Create a new screen flow and add screen element as the first element of the flow. Add the lookup element that will let the you select a user. Then add a picklist element, which will display the permission sets in the system. In order to do so, create a record choice set that will display only the permission sets. If you want the flow to display only a few permission sets and not all of them, add your criteria.
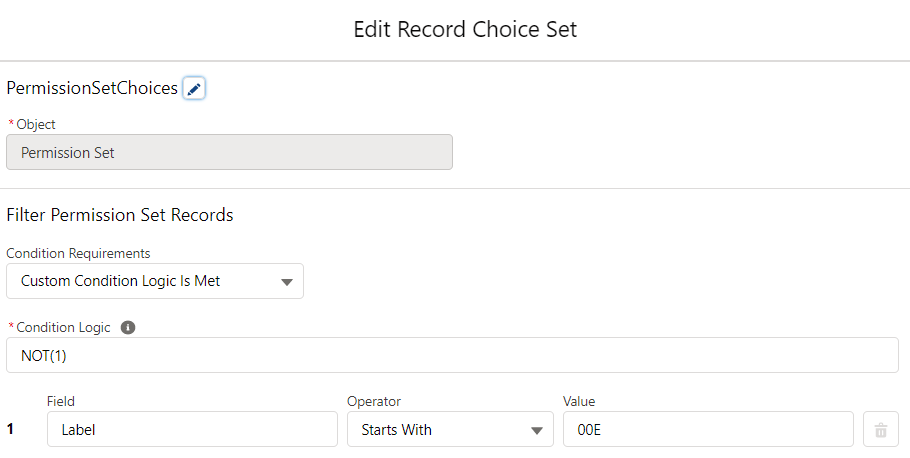
Picklist field should display the label of the permission set but store the Id of the selected record. Optionally, store the label of the selected record, it will be useful when displaying a message to the user.
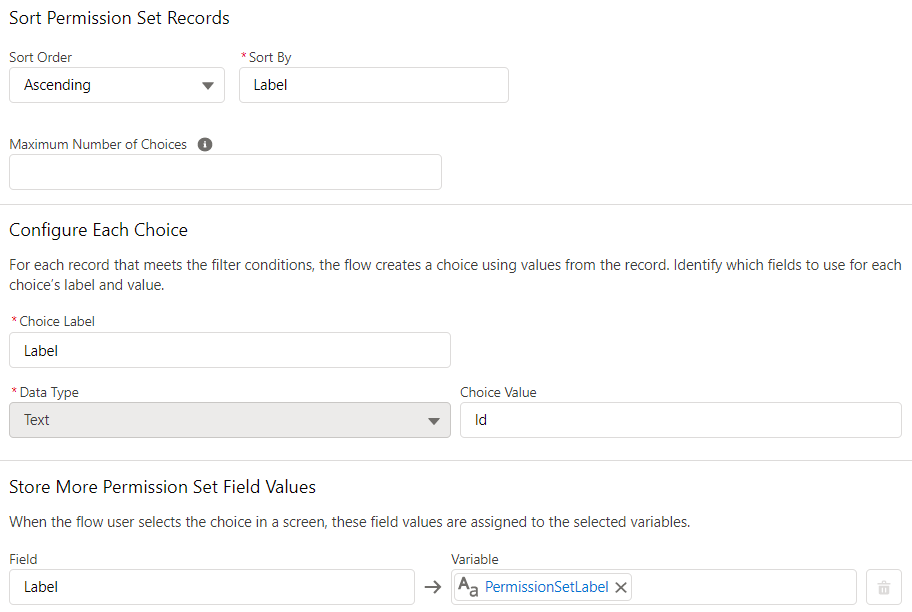
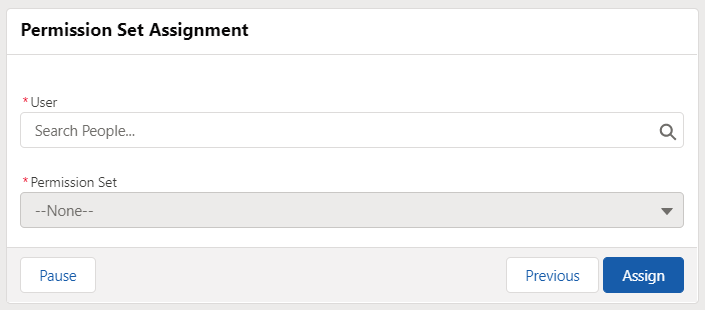
Optionally, rename the Next/Finish button as "Assign". This will make the user think that he/she doesn't need anything else to do. And yes, actually the user doesn't need to do anything else, flow will do everything.
Your screen should look like this.
Optionally, you can set an expiration date for the permission set assignment. If you do so, assigned users receive access to all aggregate permissions until the expiration date. In order to set the expiration date, add a date/time input field.
2- Add a Get Record element and get the PermissionSetAssignment record to check if the selected user already has this permission set.
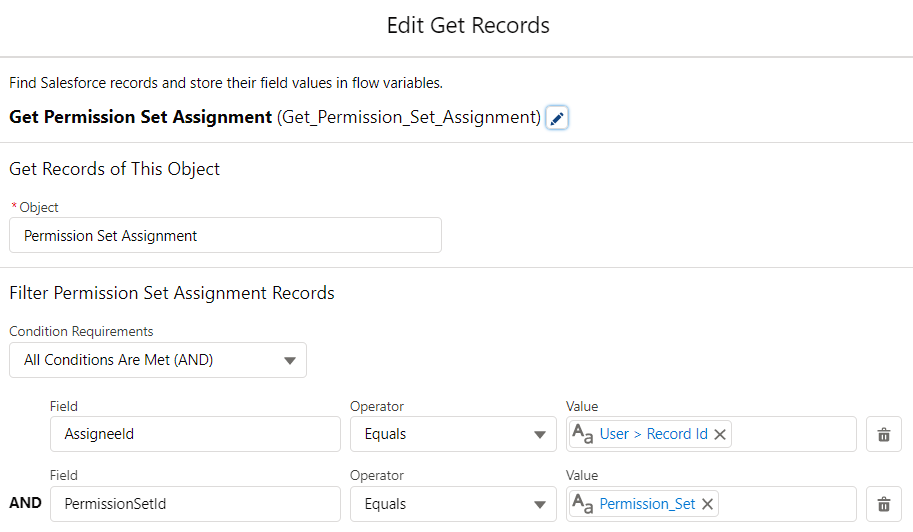
3- Add a Decision element to check if the user already has the selected permission set.
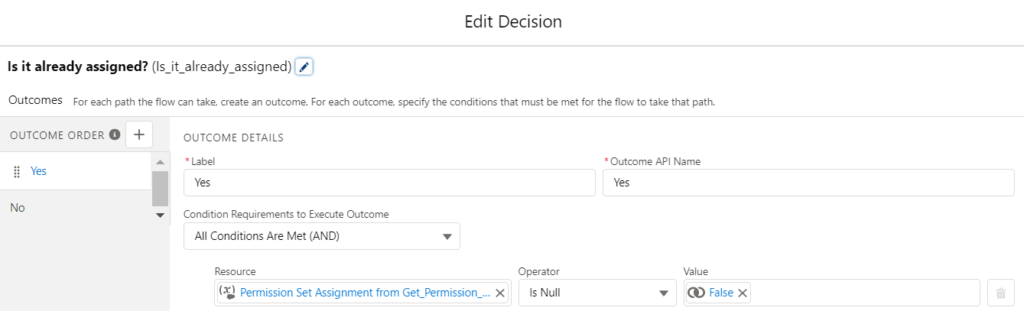
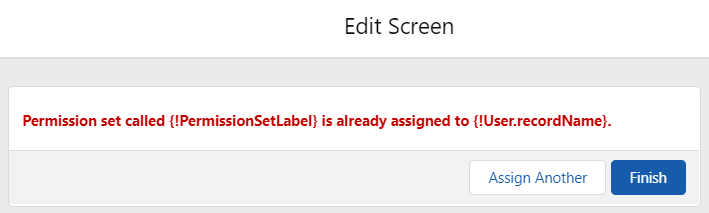
4- If it already exists, you cannot assign again. So, you will need to display a message to the user. Add a new Screen element to display a message. Optionally, rename the Previous button as "Assign Another". Since you stored the label of the selected permission set in the first step, use it in the error message. This will make the error more clear.
5- If it doesn't exist, then create a new PermissionSetAssignment record to assign the it to the selected user.
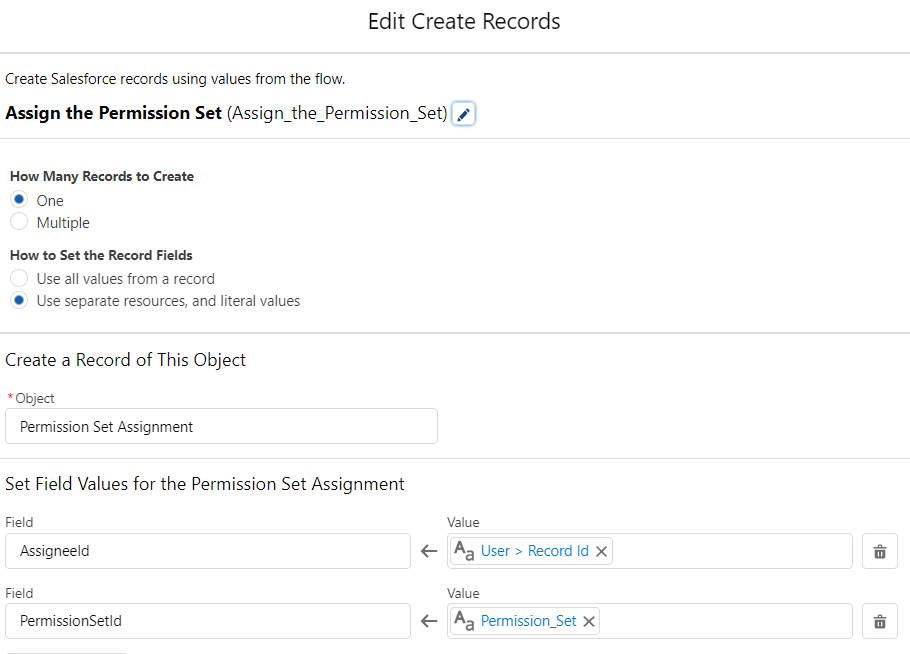
If you want to set an expiration date, don't forget to populate the ExpirationDate field.
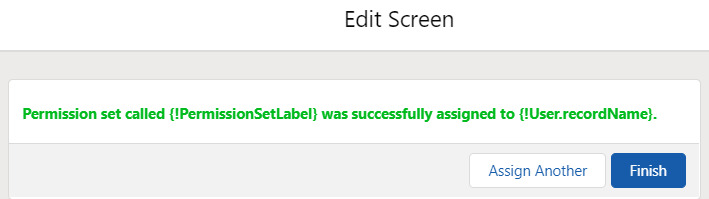
6- At the end of the flow, display a success message. Like you did in the 4th step, rename the Previous button as "Assign Another" and use variables in the message.
At the end, your flow should look like this. Optionally, make the flow run in the system context.
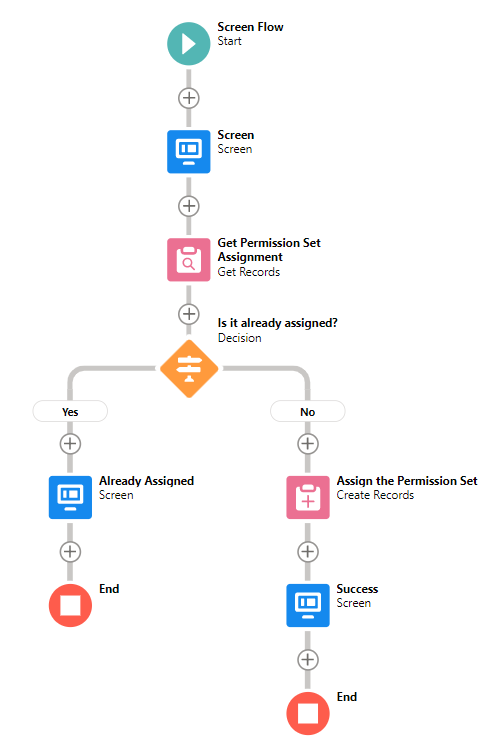
Record-Triggered Flow to Automatically Assign a Permission Set
Let's create a record-triggered flow that will automatically assign a permission set called "SSO" when a user becomes active.
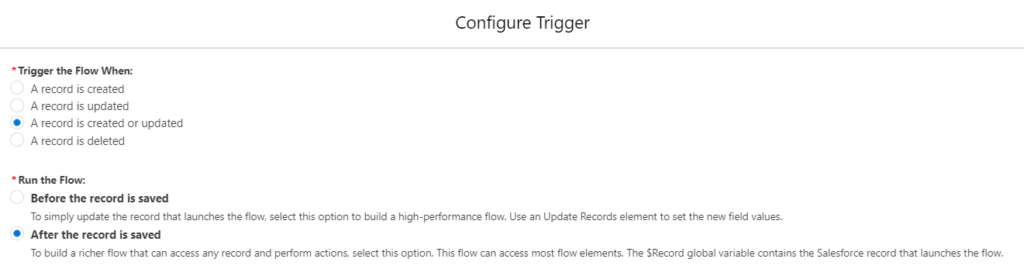
1- Create a Record-Triggered flow and choose to run it after create/update. Select User as the object and enter the criteria. So that the flow will run only when a user becomes active.
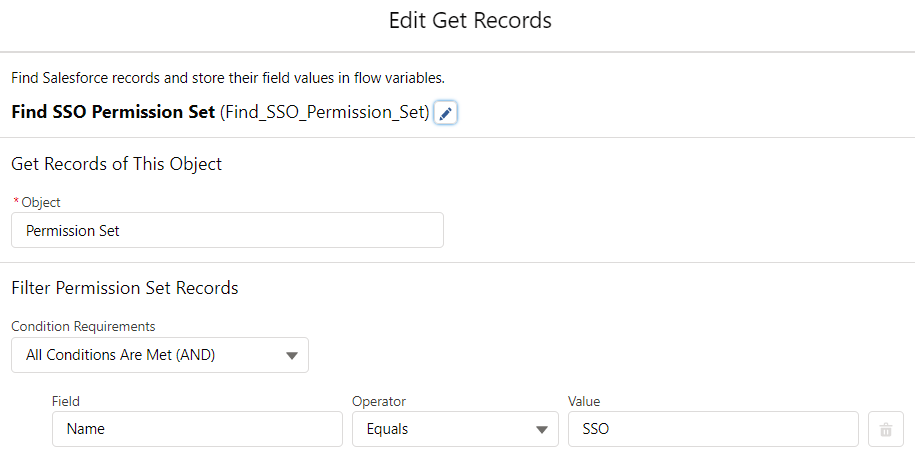
2- Add a Get Records element to get the "SSO" permission set. To assign it, you need the Id of the permission set. You can use a hardcoded value but if you do so, don't forget to change it after you deploy to other environments.
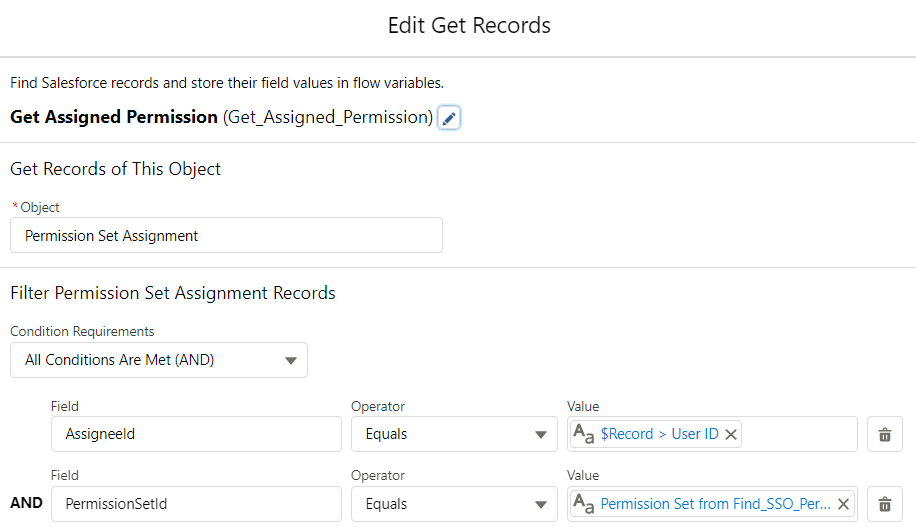
3- Add another Get Records to check if it is already assigned. In order to do so, you have to get the PermissionSetAssignment record according to the user Id and permission set Id that you got in the previous step.
4- Add a Decision element to check if the permission set is already assigned to the selected user.
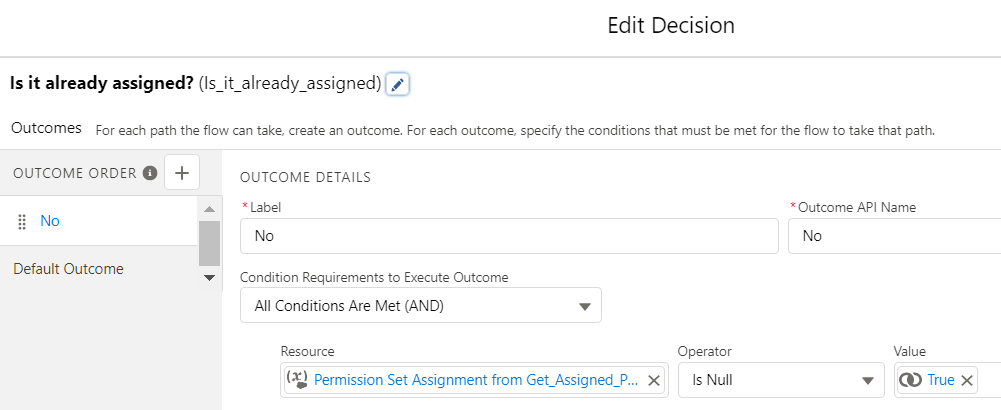
5- If it doesn't exist, then add a Create Record element to create a PermissionSetAssignment record. This action will assign the permission set to the user.
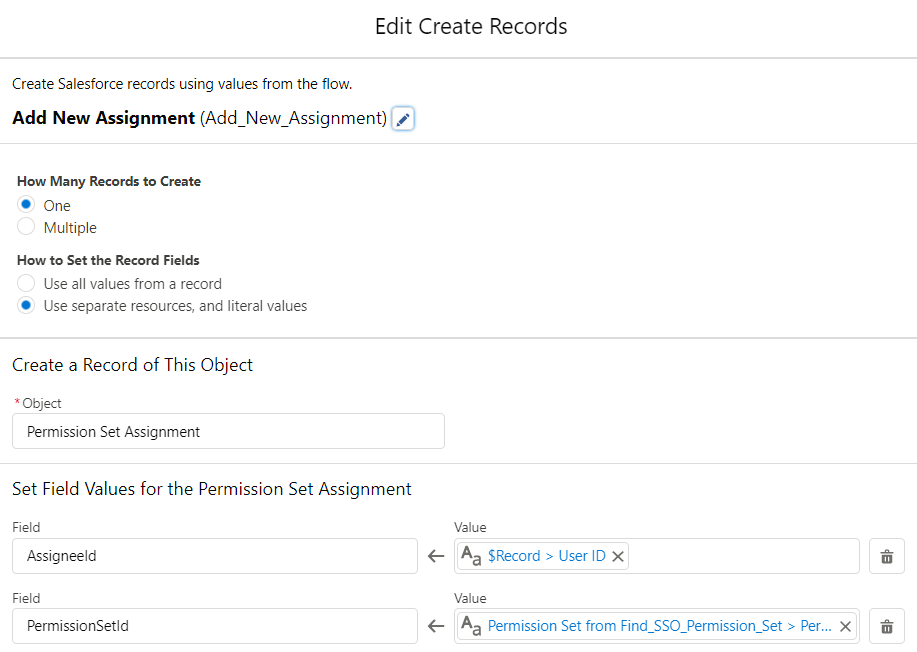
Optionally, populate the expiration date field.
At the end, your flow should look like this.
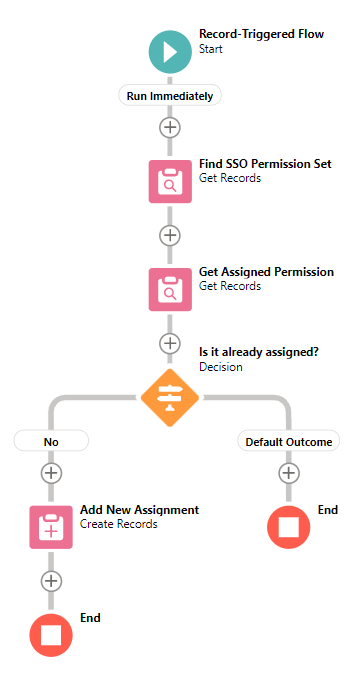
These are some simple flows to assign permission sets. You can improve them and add more logic according to your needs. Don't forget, the idea is to help the users. Try to automate the process to reduce time or give the users more capabilities that they cannot perform using the standard permission set assignment screen.
Permission Assignment Expiration Considerations
If you set the ExpirationDate field on the PermissionSetAssignment record, assigned users receive access to all aggregate permissions until the expiration date. It means that, after the expiration date, user will not have those permissions anymore. However, PermissionSetAssignment record will still exist in the system as inactive.
Assignments that expire are treated as soft-deletes. Moreover, SOQL queries don’t return the expired permission set assignments. You can still retrieve them using the ALL ROWS clause. However, there is no standard option to use ALL ROWS clause in flow. Therefore, your Get Records element will not find the expired permission set assignments. This may cause an issue because if you try to create a PermissionSetAssignment record, the system will say that it is a duplicate value.
Read this post to learn how to use flow to assign a permission set with an expiration date.
17 Comments
But for standard user who without "Assign Permission Sets" AND "View Setup and Configuration", is this approach still available?
If you run the flow in the system context, then any user can run this flow and assign permission sets. I tried now and it is working.
Adding to Wayne's comment, even running in the system context, the 'non admin' user receives this error: "An error occurred while trying to update the record. Please try again. insufficient access rights on cross-reference id" I think they need Modify User permissions for this to actually work? Also tried updating another custom field on the User Object and received the same message. I don't think non-admin users have access, even if the Flow is running as System.
Hi Marcus, I tried it again with a non-admin user and it worked. However, I tried it with another user that has Salesforce Platform license, it didn't work for that user. I thought it was related to the license but then I saw that the user didn't have the Run Flows permission. After giving the permission, it worked for that user as well. So I can say that it is working for non-admin users too.
Thank you for this, it was very helpful.
I have followed the guidance for a Record Triggered Flow but got an error - This error occurred when the flow tried to create records: INVALID_CROSS_REFERENCE_KEY: We can't save this assignment because there's no permission set ID or permission set group ID.. You can look up ExceptionCode values in the SOAP API Developer Guide.
Are you able to advise?
In the step that the flow fails, do you see the permission set id? Looks like it is missing, at least it is what I understand from this error message.
If you set an expiration on the permission set and the permission set expires, the permission set assignment record persists. However, when you query the Permission Set Assignment object, you *cannot* retrieve the expired record, so you'll always get a duplicate permission set assignment error when trying to recreate the assignment.
Have you seen the same?
Hi Adam, Yes, that's right. In the official documentation it says "SOQL queries don’t return user assignment information for permission assignments that expire. Assignments that expire are treated as soft-deletes. You can retrieve the expiring assignment information using the ALL ROWS clause." So it is not possible to find this record using standard elements of flow. However, when you try to create a new one, it will say that it is duplicate. I think we may need an Apex action for this. I will try to find a solution.
I found a solution for this issue and wrote a post. Let me know if it answers your question.
https://salesforcetime.com/2023/05/04/using-flow-to-assign-a-permission-set-with-an-expiration-date/
My screen one is all good but for some reason the RTF is getting flagged at the Get permission Assignment Element more specifically the PermissionSetID EQUALS Permission Set From, can you explain what that is supposed to be?
Find all PermissionSetAssignment records where
AssigneeId Equals {!$Record.Id} (005Dn0000075DESIA2) AND PermissionSetId Equals {!Find_AC_Permission_Set.PermissionsViewDeveloperName} (false) Store the values of these fields in Get_Permission_Set_Assignment: Id Result
Info Failed to find records.
Hi, I see a problem here: PermissionSetId Equals {!Find_AC_Permission_Set.PermissionsViewDeveloperName} (false) You have to use the Id of the permission set.
Hi, I am attempting to assign two permissions sets with record triggered Flow, but I am keep getting an error. "This error occurred when the flow tried to create records: INVALID_CROSS_REFERENCE_KEY: We can't save this assignment because there's no permission set ID or permission set group ID.. You can look up ExceptionCode values in the SOAP API Developer Guide."
Hi, From the error message, I understand that the permission set id is missing. Can you check if you mapped that field?
Thank you for the article. Very helpful.
Would there be a way to add more than 1 permission while creating a new user in a flow?
For instance, I usually setup new users similarly to another user. This user may have 3 permission sets. Can I add all 3 at the same time, or would I need to build in the "Assign Additional Permissions" button like you did in the article?
You can get all these 3 permission sets, then use loop and assignment elements in order to prepare a PermissionSetAssignment collection in the flow. Then you can create all of them at once.
How can send email option to the end of the flow, after user assigned to a permission set?
Hi, I didn't understand the question well, but you can send an email using the Send Email core action.
2 Trackbacks / Pingbacks
- What does Group role mean? – Answersglobe
- Using Flow to Assign a Permission Set with an Expiration Date - Salesforce Time
Leave a Reply Cancel reply
Your email address will not be published.
Save my name, email, and website in this browser for the next time I comment.
Copyright © 2024 | SalesforceTime.com
- Marketing Cloud
Experiences
Access Trailhead, your Trailblazer profile, community, learning, original series, events, support, and more.
Tooling API
Spring '24 (API version 60.0)
Search Tips:
- Please consider misspellings
- Try different search keywords
PermissionSetAssignment
Supported soap api calls.
create() , delete() , describeSObjects() , query() , retrieve() , update() , upsert()
Supported REST API Methods
DELETE, GET, HEAD, PATCH, POST, Query
Special Access Rules
As of Summer ’20 and later, only users who have one of these permissions can access this object:
- View Setup and Configuration
- Assign Permission Sets
- Manage User

COMMENTS
Assign Custom Record Types in Permission Sets. As an admin, you can help your organization succeed by staying up to date with the latest Salesforce releases and getting familiar with product enhancements. Check out the Summer '24 release notes for a list of new features and available updates.
If I set it to MASTER then if I only have one record type on the permission set it will skip the record type selection screen (good) but default to MASTER and ignores the permission set (bad). It appears that these need to have 1 non-master record type on the profile otherwise it skips past that screen from the permission set.
You cannot restrict permissions by adding a permission set to a user. Permissions are "additive", meaning they are all combined together; the most permissive set of permissions for a user determines what capabilities they have. You would have to remove it from the profile and assign it via a different permission set.
Object permissions determine the baseline level of access for all the records in an object. Org-wide defaults modify those permissions for records a user doesn't own. Org-wide sharing settings can be set separately for each type of object. Org-wide defaults can never grant users more access than they have through their object permission.
I am trying to create a permission set using metadata api. in permission sets we have the record type assignment. so i am trying to assign some recordtypes to the permission set. but unfortunately in the metadata api developer guide i do not see a metadata type for the recordtype assignments in permission sets. -
Aim: Have 2 record types with 2 page layouts for 2 groups of users of the same profile for a custom object but ensuring each group are not faced with a record type selection/prompt upon record creation. What I have done: Created my record types + associated page layouts and 2 permission sets - 1 for group A with record type A access only and 1 for group B with record type B access only.
1. You have to pick an object to assign record types for. So, Setup > Profiles > Profile Name > Object Settings > Object Name > Edit. Note that this is only true if you have the Enhanced Profile Editor. The notes you're looking at are written for the "classic" editor, which presented all options on a single page. Classic view:
Solution: use Permission Set. Create a new permission set and assign it to that Sales support. When you are in the Permission Set, select Object Settings, for the object (in this case is Accounts ), you will see Account: Record Type Assignments and enable Not-normal record type. Then assign the permission set to that sales support user, I'll ...
In setup>opportunities>record types, both are active, I can't figure out how to enable this. I can set page layout assignments. I can make the field visible on the page layout. But I can't create or edit an opportunity to this record type, I think because the record type is not enabled for any of my users. I think I can create a new permission ...
For example, there's an Account Record Type that is included as part of our managed package. I want to make this Record Type "visible" in the Permission Set as part of the post-install task. I cannot figure out the mechanism for doing this via Apex code. In fact, I'm not sure it is supported. There doesn't seem to be an SObject equivalent to ...
To see if the user is assigned to the permission set, we need to query the Permission Set Assignment object with another Get Records element to find a record with the user and the permission set. If a permission set assignment record is found, then we'll take the assignee ID and store it in the variable varUserHasPermissionSet.
Master defaulted on the profile + only 1 custom record type on a permission set - the user will skip the jump screen and the custom record type will automatically be set on the newly created record. Master defaulted on the profile + > 1 custom record type on one or more permission sets - the user will get the jump screen every time in order to ...
1- Create a Record-Triggered flow and choose to run it after create/update. Select User as the object and enter the criteria. So that the flow will run only when a user becomes active. 2- Add a Get Records element to get the "SSO" permission set. To assign it, you need the Id of the permission set.
Description. The date that the assignment of the permission set or permission set group expires for the specified user. This field is available in API version 52.0 and later. IsActive. Type. boolean. Properties. Defaulted on create, Filter, Group, Sort. Description.