
- IT Administration Forum
- PowerShell Forum
- Community Forum
- PowerShell Group
- Earning as 4sysops member
- Member Ranks
- Member Leaderboard – This Month
- Member Leaderboard – This Year
- Member Leaderboard – All-time
- Author Leaderboard – 30 Days
- Author Leaderboard – 365 Days
- Cloud Computing
- Write for 4sysops
- User rights assignment in Windows Server 2016
4sysops - The online community for SysAdmins and DevOps

Built-in local security principals and groups
Center for internet security, local policies/user rights assignment.
- Recent Posts
- KeePassXC: A free cross-platform password manager - Wed, Jun 5 2024
- Improve Windows performance with Microsoft PC Manager - Mon, Apr 8 2024
- Verify digital file signature with SigCheck - Mon, Mar 4 2024
Security policy settings are sets of rules that control various aspects of protection. They include account policies, local policies, user rights assignment, the Windows firewall, software restrictions, and so on. There are several ways to configure security policy settings. The most common are:
- Group policy objects (GPO) – Used in Active Directory domains to configure and regularly reapply security settings to multiple computers.
- Local security policy (secpol.msc) – Used to configure a single (local) computer. Note that this is a one-time action. If another administrator changes these settings, you will need to manually change them back to the required state.
As most organizations use an Active Directory domain, it is preferred to apply security settings via group policies. You should have at least three security baselines created and linked in your domain, based on the following machine types:
- Domain Controllers (DC)
- Member Servers (MS)
- User Workstations

Configuring user rights assignment via Goup Policy
If you have multiple versions of operating systems (OS) running on these machines, you should create separate baselines for each OS version, as some settings might not be available. This also enables stricter configuration for older systems, as they are usually less secure.
It is a best practice to configure security policies using only built-in local security principals and groups, and add needed members to these entities. This gives you much better visibility and flexibility, as GPO provides more options to manage local group members, than to manage security policy members. For example, it's not possible to add a group whose name is generated using system variables (e.g., LAB\LocalAdmins_%COMPUTERNAME%) to a security policy; however, the group can be added to the Administrators group itself.

Security policies do not support generated group names
- Administrators – Members of this group have full, unrestricted access to the computer. Even if you remove some privileges from the Administrators group, a skilled administrator can still bypass those settings and gain control of the system. Only add highly trusted people to this group.
- Authenticated Users – A special security principal that applies to any session that was authenticated using some account, such as a local or domain account.
- Local account and member of Administrators group – A pseudogroup available since Windows Server 2012 R2. It applies to any local account in the Administrators group and is used to mitigate pass-the-hash attacks (lateral movement).
- Remote Desktop Users – Members of this group can access the computer via Remote Desktop services (RDP).
- Guests – By default, this group has no permissions. I don't think there is any need to use the Guest account and group today.
The Center for Internet Security (CIS) is a well-known non-profit organization that focuses on cybersecurity. To improve your knowledge of cybersecurity, you can access their free materials:
- CIS Controls – A set of 20 basic and advanced cybersecurity actions (controls). Using these, you can stop the most common attacks.
- CIS Benchmarks – Guidelines with specific configuration steps and detailed explanations. CIS Benchmarks are available for various products such as Windows Server, SQL Server, Apple iOS, and many more.
Both can be downloaded in exchange for your email address. There's no need to worry—there will be no further email, unless you choose to receive them.
Many companies and institutions create their security baselines based on CIS. I recommend you read CIS Controls. It really helped me to understand the importance of various security actions and settings.

CIS Benchmarks example
User rights assignments are settings applied to the local device. They allow users to perform various system tasks, such as local logon, remote logon, accessing the server from network, shutting down the server, and so on. In this section, I will explain the most important settings and how they should be configured.
For each setting, the following format is used:
Name of the setting: Recommended value, or values
Access Credential Manager as a trusted caller: No one (empty value)
Access to the Credential Manager is granted during Winlogon only to the user who is logging on. Saved user credentials might be compromised if someone else has this privilege.
Access this computer from the network: Administrators, Authenticated Users
Required for users to connect to the computer and its resources, such as an SMB share, shared printers, COM+, etc. If you remove this user right on the DC, no one will be able to log on to the domain.
Note : On DCs, you should also add the “ENTERPRISE DOMAIN CONTROLLERS“ group.
Allow log on locally: Administrators
The default configuration includes the Users group, which allows a standard user to log on to the server console. Limit this privilege only to administrators.
Allow log on through Remote Desktop Services: Administrators, Remote Desktop Users
It's common practice that some applications are used via RDP sessions by standard users. This privilege is also frequently required for remote assistance offered by an organization's helpdesk. If a server is running Remote Desktop Services with the Connection Broker role, the Authenticated Users group must also be added to this privilege.
Note: On the DC, it is recommended to allow only administrators to connect via RDP.
Back up files and directories: Administrators
This is a sensitive privilege that allows a user to bypass NTFS permissions (only via an NTFS API interface, such as NTBACKUP). A malicious user could backup and restore data on a different computer, thereby gaining access to it.
Deny access to this computer from the network/Deny log on through Terminal Services: Local account and member of Administrators group, Guests
The default value is only Guests. You should add the second group to prevent pass-the-hash attacks, so if a local elevated user is compromised, it cannot be used to elevate privileges on any other network resource, or access it via RDP.
Force shutdown from a remote system/Shut down the system: Administrators
Only administrators should be able to shut down any server, to prevent denial-of-service (DoS) attacks.
Manage auditing and security log: Administrators
This is a sensitive privilege, as anyone with these rights can erase important evidence of unauthorized activity.
Note: If you are running MS Exchange, the “Exchange Servers” group must be added to DCs.
Restore files and directories: Administrators
Attackers with this privilege can overwrite data, or even executable files used by legitimate administrators, with versions that include malicious code.
Take ownership of files or other objects: Administrators
User having this privilege can take control (ownership) of any object, such as a file or folder, and expose sensitive data.
Deny log on as a batch job/Deny log on as a service/Deny log on locally: Guests
To increase security, you should include the Guests group in these three settings.
Debug programs/Profile single process/Profile system performance: Administrators
This setting allows a user to attach a debugger to a system or process, thereby accessing critical, sensitive data. It can be used by attackers to collect information about running critical processes, or which users are logged on.
Change the system time: Administrators, Local Service
Changes in system time might lead to DoS issues, such as unavailability to authenticate to the domain. The Local Service role is required for the Windows Time service, VMware Tools service, and others to synchronize system time with the DC or ESXi host.
Create a token object: No one (empty value)
Users with the ability to create or modify access tokens can elevate any currently logged on account, including their own.
Impersonate a client after authentication: Administrators, Local Service, Network Service, Service
An attacker with this privilege can create a service, trick a client into connecting to that service, and then impersonate that account.
Note: For servers running Internet Information Services (IIS), the "IIS_IUSRS" account must also be added.
Load and unload device drivers: Administrators
Malicious code can be installed that pretends to be a device driver. Administrators should only install drivers with a valid signature.
I hope this article helped you to understand why it is important to define a security baseline for your systems. Many of the settings are already configured properly following server deployment; however, if they are not controlled by a GPO, they can be manipulated by malicious users. Be careful to whom you grant administrator permissions.
IT Administration News
- Code security configurations can now be enforced – The GitHub Blog
- PHP fixes critical RCE flaw impacting all versions for Windows
- Configuration Manager technical preview version 2405 – Microsoft Community Hub
- Apple to launch a new Passwords app at WWDC 2024, states report – Neowin
- Microsoft Research chief scientist has no issue with Recall The Register
Read All IT Administration News
Join our IT community and read articles without ads!
Do you want to write for 4sysops? We are looking for new authors.
- Windows Server security features and best practices
- Security options in Windows Server 2016: Accounts and UAC
- Security options in Windows Server 2016: Network security

Enable Microsoft Entra ID passkey authentication
KeePassXC: A free cross-platform password manager

Configuring external authentication methods in Microsoft 365 with Microsoft Entra ID

Integrate Microsoft Graph activity logs for Microsoft 365 with Azure Monitor

Disable Basic Authentication for SMTP AUTH in Exchange Online

Rotate BitLocker recovery passwords, delete used keys from Active Directory
Delegate permission to unlock Active Directory accounts

Partition Windows drive in WinPE using PowerShell

Allow end users to execute code on the Windows logon screen with administrator privileges
New mitigations for CVE-2023-24932 (BlackLotus) in the April update, not yet enabled by default

Combining password policies for Active Directory and Entra ID (Azure AD)

Create, use, and manage Windows Passkeys
Improve Windows performance with Microsoft PC Manager

Encrypt and decrypt with Ansible Vault
Critical alert: SSH and XZ vulnerability (CVE-2024-3094) – Testing and remediation
Forgot BitLocker PIN: recover encrypted drive

Privacy settings in Microsoft Edge: disable tab grouping, follow creators, similar sites, and shopping recommendations

Convert certificate format with OpenSSL
Verify digital file signature with SigCheck

Sudo for Windows vs. Runas and Sudo for Linux
Created a domain account to use as a service account and then tried to run powershell cmdlets against the active RDS management server.
Gave that account local admin access on the broker servers and then was able to get further.
Got the error “Access is denied” when trying to run the invoke-RDUserLogoff(with correct hostserver and unifiedsessionID values) to log off a session using that account.
Need to know what permissions should be granted to the account to provide ability to run this command and where like on the broker or the session host.
I can’t run the RD cmdlets on the RD broker to remove a user session without local administrator privileges on the broker and session host.
I need to know what user permissions are necessary to run these cmdlets as giving local admin is not desired.
Sir we are having user1 in server1. We want to collect logs of server1 from server2 using credentials of user1. Surprisingly even after entering the credentials of user1 in event viewer it is taking loggedin credentials of the user logged into server2.
Leave a reply Click here to cancel the reply
Please enclose code in pre tags: <pre></pre>
Your email address will not be published. Required fields are marked *
Notify me of followup comments via e-mail. You can also subscribe without commenting.
Receive new post notifications

Subscribe to Newsletter
Follow 4sysops.
Please ask IT administration questions in the forums . Any other messages are welcome.
Log in with your credentials
or Create an account
Forgot your details?
Create account.
WinSecWiki > Security Settings > Local Policies > User Rights
User Rights Assignments
Although in this section they are called user rights, these authority assignments are more commonly called privileges.
Privileges are computer level actions that you can assign to users or groups. For the sake of maintainability you should only assign privileges to groups not to individual users. Each computer has its own user rights assignments. In particular this means you should be cognizant of rights assignments on member servers which may easily differ from the rights assignments you find on your domain controllers. To centrally control user rights assignments on computers throughout your domain use group policy.
- Logon rights
- Admin equivalent rights
- Tracking user rights with the security log
- User rights in-depth
- Access this computer from the network
- Act as part of the operating system
- Add workstations to domain
- Adjust memory quotas for a process
- Allow log on locally
- Allow logon through Terminal Services
- Back up files and directories
- Bypass traverse checking
- Change the system time
- Create a pagefile
- Create a token object
- Create global objects
- Create permanent shared objects
- Debug programs
- Deny access to this computer from the network
- Deny logon as a batch job
- Deny logon as a service
- Deny logon locally
- Deny logon through Terminal Services
- Enable computer and user accounts to be trusted for delegation
- Force shutdown from a remote system
- Generate security audits
- Impersonate a client after authentication
- Increase scheduling priority
- Load and unload device drivers
- Lock pages in memory
- Log on as a batch job
- Log on as a service
- Manage auditing and security log
- Modify firmware environment values
- Perform volume maintenance tasks
- Profile single process
- Profile system performance
- Remove computer from docking station
- Replace a process level token
- Restore files and directories
- Shut down the system
- Synchronize directory service data
- Take ownership of files and other objects
Child articles:
- Logon Rights
- Admin Equivalent Rights
- Tracking User Rights with the Security Log
- User Rights In-Depth
Back to top
| • | |
| • | |
| • | |
| • |

Stack Exchange NetworkStack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers. Q&A for work Connect and share knowledge within a single location that is structured and easy to search. Can't edit Local Security PolicyI'm trying to add users to the Access this computer from the network User Rights Assignment policy but the 'Add' button is disabled:  I'm connecting to the machine via RDP using the local Administrator account (not a domain user). I've also tried to do the same with a domain user that is in the Administrators group but the result is the same. How can I add a user to this policy? The machine is running Windows 7.
You cannot edit this User Rights Assignment policy because this setting is being managed by a domain-based Group Policy. In this case, the domain Group Policy setting has precedence and you are prevented from modifying the policy via Local Group Policy. To modify this policy, either:
You must log in to answer this question.Not the answer you're looking for browse other questions tagged windows security remote-desktop administrator group-policy ..
Hot Network Questions
Set and Check User Rights Assignment via PowershellYou can add, remove, and check user rights assignment (remotely / locally) with the following powershell scripts.. Posted by : blakedrumm on Jan 5, 2022 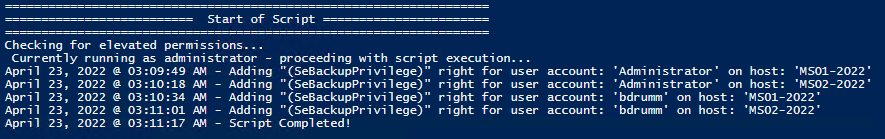 Local ComputerRemote computer, output types. This post was last updated on August 29th, 2022 I stumbled across this gem ( weloytty/Grant-LogonAsService.ps1 ) that allows you to grant Logon as a Service Right for a User. I modified the script you can now run the Powershell script against multiple machines, users, and user rights. Set User RightsHow to get it. All of the User Rights that can be set:
Note You may edit line 437 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE. Here are a few examples: Add Users Single Users Example 1 Add User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -AddRight -UserRight SeInteractiveLogonRight Example 2 Add User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Add User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Add User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -AddRight -Username S-1-5-11 -UserRight SeBatchLogonRight Add Multiple Users / Rights / Computers Example 5 Add User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -AddRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2 Remove Users Single Users Example 1 Remove User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -RemoveRight -UserRight SeInteractiveLogonRight Example 2 Remove User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Remove User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Remove User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -RemoveRight -Username S-1-5-11 -UserRight SeBatchLogonRight Remove Multiple Users / Rights / Computers Example 5 Remove User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -RemoveRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2 Check User RightsIn order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play. 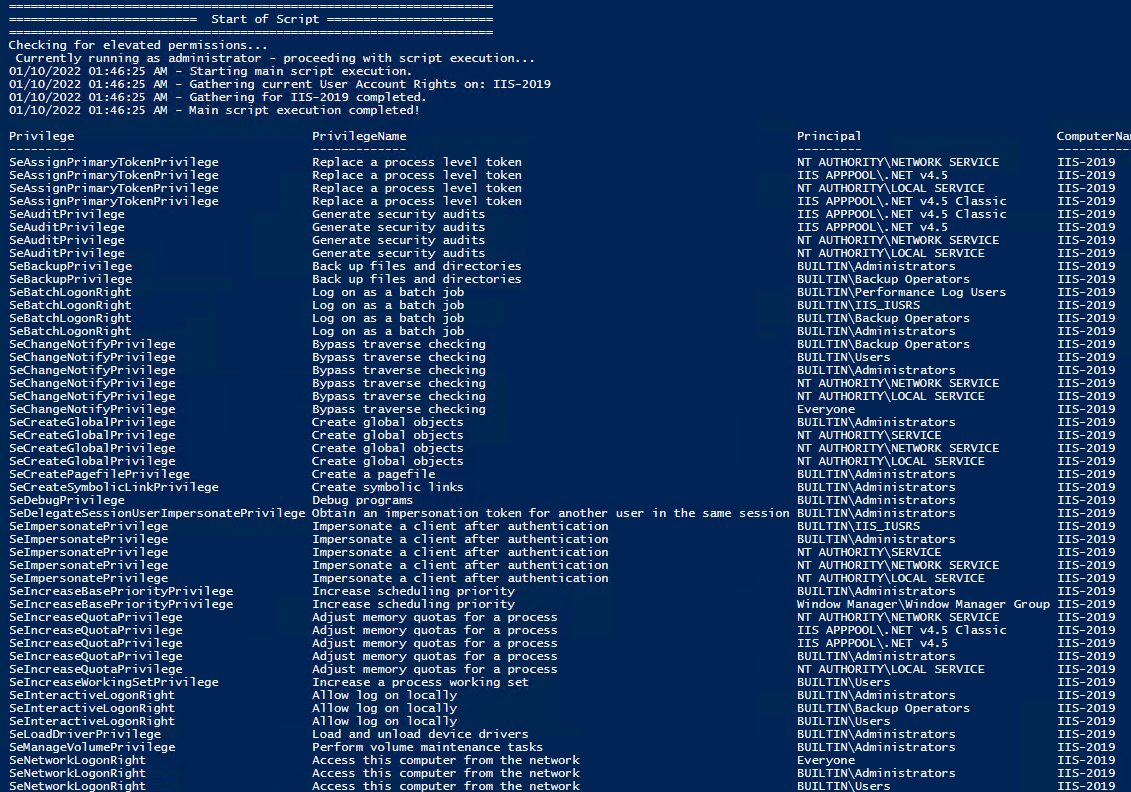 Note You may edit line 467 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE. Get Local User Account Rights and output to text in console: Get Remote SQL Server User Account Rights: Get Local Machine and SQL Server User Account Rights: Output Local User Rights on Local Machine as CSV in ‘C:\Temp’: Output to Text in ‘C:\Temp’: PassThru object to allow manipulation / filtering: I like to collaborate and work on projects. My skills with Powershell allow me to quickly develop automated solutions to suit my customers, and my own needs. Email : [email protected] Website : https://blakedrumm.com My name is Blake Drumm, I am working on the Azure Monitoring Enterprise Team with Microsoft. Currently working to update public documentation for System Center products and write troubleshooting guides to assist with fixing issues that may arise while using the products. I like to blog on Operations Manager and Azure Automation products, keep checking back for new posts. My goal is to post atleast once a month if possible.
All about Microsoft Intune Peter blogs about Microsoft Intune, Microsoft Intune Suite, Windows Autopilot, Configuration Manager and more  Restricting the local log on to specific usersThis week is about restricting the local logon on Windows devices to specific users. Not because it is something particularly new, but simply because it is been an ask every now and then. Think about further locking down a kiosk device, for example. Restricting the local logon can be achieved by either only allowing specific users to log on, or by denying specific users to log on. In other words, whitelisting versus blacklisting. The allow-option is basically a whitelist and the deny-option is basically a blacklist. When looking at restricting the local logon, a whitelist is the easiest method to get quickly really restrictive, as only the users on the list are allowed to log on locally. Luckily, nowadays there is easy method for configuring such a whitelist with users that are allowed to log on locally on a Windows device. This post will provide some more details around that configuration, followed with the configuration steps. This post will end with showing the user experience. Note : Keep in mind that this post is focussed on the local log on on Windows devices and not the remote log on. Configuring the allow local log on settingWhen looking at configuring the allow local log on configuration, the UserRights section in the Policy CSP is the place to look. That section contains many of the different policy settings of the User Rights Assignment Local Policies , including the Allow log on locally ( AllowLocalLogOn ) policy setting. That policy setting can be used to configure the users that are allowed to locally log on to the Windows device. Besides that, it’s also good to mention that with the latest Windows 11 Insider Preview Builds, this section of the Policy CSP, is getting more and more policy settings. Nearly all of the User Rights Assignment Local Policies are now available for configuration, including Logon as a service , Logon as a batch job , and many more. Maybe even better, all of these available policy settings – including the new policy settings that are currently still in preview – are now configurable via the Settings Catalog profile (as shown below in Figure 1). 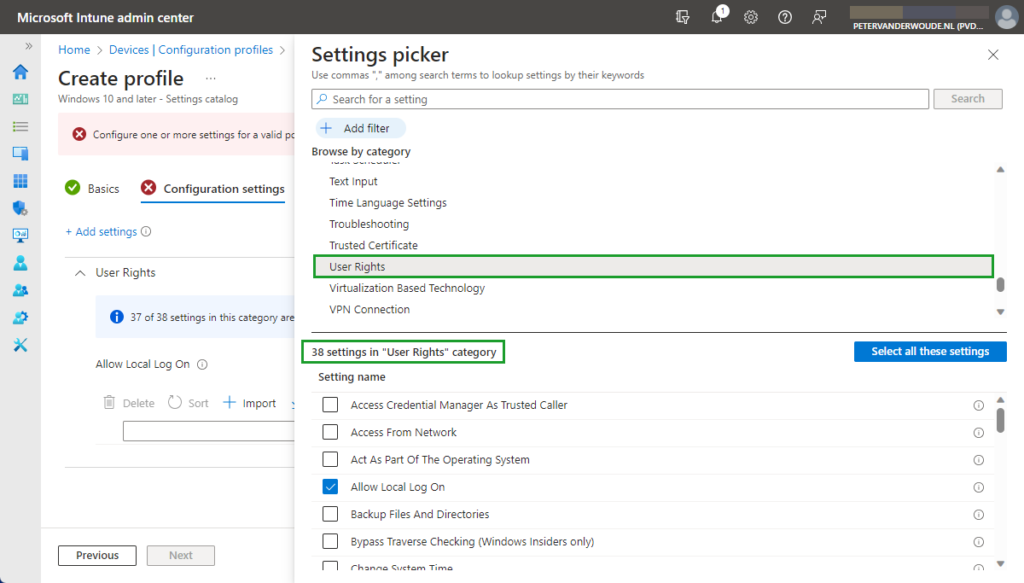 After being familiar with the available policy settings and the configuration profile, the configuration of those policy settings is pretty straight forward. The following eight steps walk through the creation of a Settings Catalog profile that contains the required setting to configure the local logon, by using the Allow log on locally policy setting.
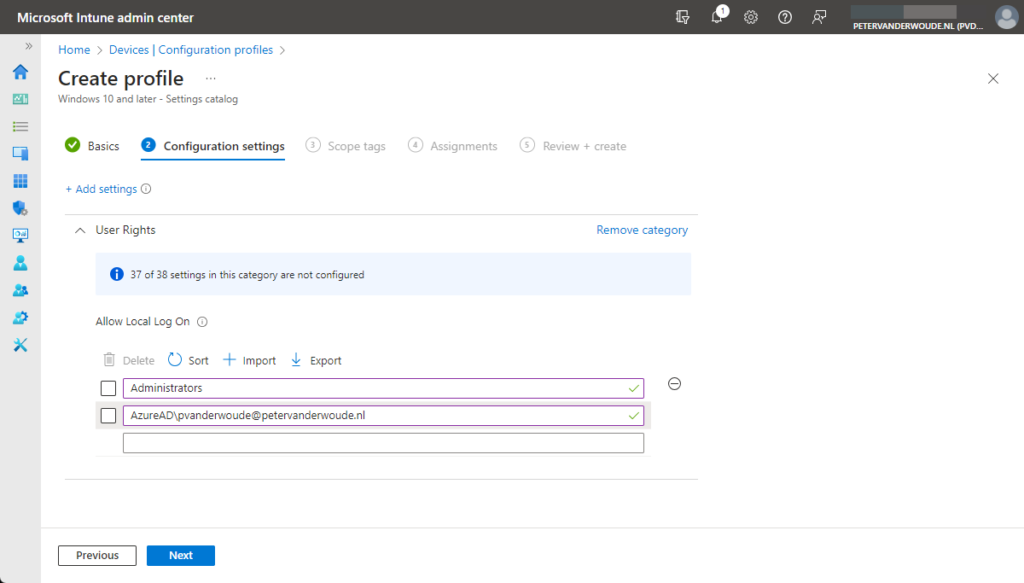
Note : As these settings are now configurable via the Settings Catalog , that also takes away the challenges with multiple entries. No need to manually specify a delimiter, as Microsoft Intune takes care of that. Experiencing the user rights configurationAfter configuring the users that are allowed to log on locally to the Windows device, it’s pretty straight forward to experience the behavior. Simply try to log on to that device with a user account that is not allowed to log on locally. That will provide an experience as shown below in Figure 3. The user will receive the notification that the sign-in method is not allowed. Besides that, it’s also important to be familiar with the side effects of this configuration. The most important side effect is the impact on the self-service capabilities, like self-service PIN reset and self-service password reset. That’s simply because those capabilities rely on the temporary account defaultuser1 and that account won’t be able to log in, as only the specified users are allowed to locally log on to the Windows device. That experience is shown below in Figure 4. The user will either receive the status message of 0xc000015b , or will simply be switched back to the logon screen. 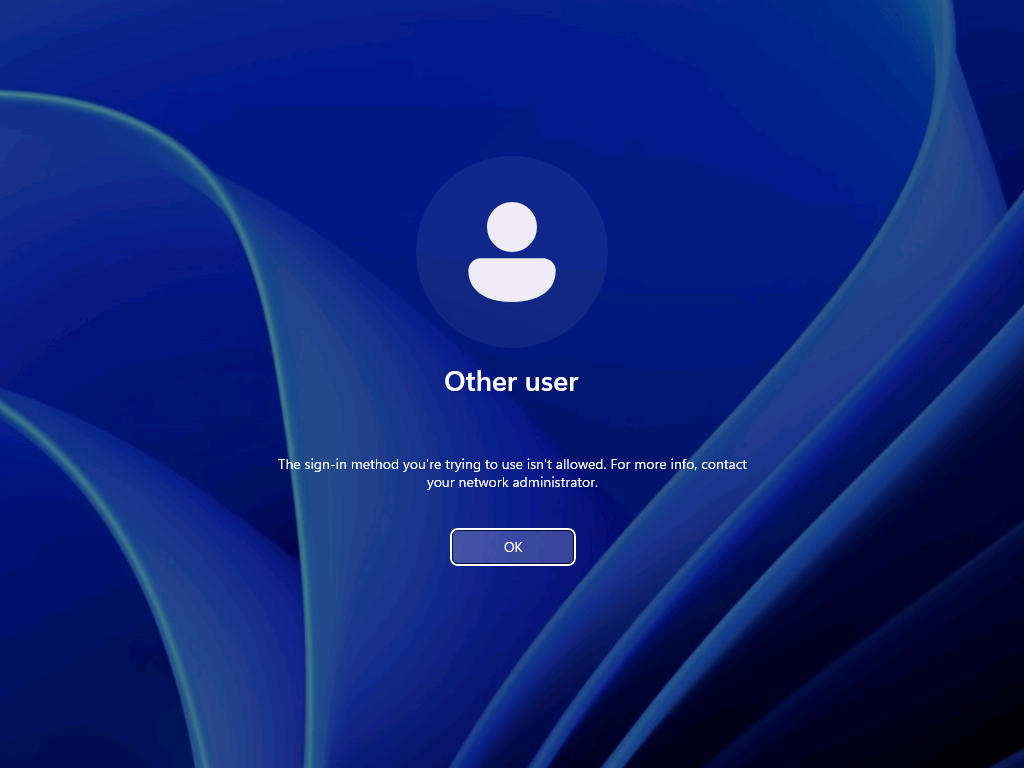 Note : The failed log on information is registered in the Security log in the Event Viewer with Event ID 4625 . More informationFor more information about the user rights configuration options, refer to the following docs.
25 thoughts on “Restricting the local log on to specific users”I’d like to contribute to this. This method does not inherently allow you to specify an EntraID group of users that you wish to deny local logon (at least it didnt use to) however i’ve found that if you use “account protection” policies populate the local group “Guests” with users from an EntraID group you can use the above stated policy to in effect acheive deny local logon for an EntraID group of users. (Via denying the local group “guests” as stated in your blog) I use this in production, works well Thank you for that suggestion, Temilit. Regards, Peter I have not been able to replicate this. I followed inthecloud247’s blog post on this, but the only SID I was able to add to the Guests local group was the SID of an AAD directory role, and not one of an AAD security group. Which version of Windows are you using? Regards, Peter
Can you use an AAD group here? Not at this moment, Henrik. Regards, Peter Is there currently a way to restrict interactive log in but allow elevation log in prompts? I would like to prevent Intune Admins from logging in locally but still allow elevation for installs/CMD. Not sure you can achieve that with this policy, but I haven’t looked really deep in that use case yet. Regards, Peter
Is there a way to specify an EntraID security group with this settings? Hi Yoni, The last time I tried that was not possible yet. Regards, Peter Is there a way sign in KioskUser0 automatically using User Rights? Hi Mo, Can you provide some more details about what you’re trying to achieve? Regards, Peter We have deployed Self-Deploy AutoPilot profile plus Kiosk Configuration Profile for single app and then assign to dynamic device group. The Self-Deploy AutoPilot process completes without any issues and Kiosk policy is applied to the device. However, the KioskUser0 should auto logging automatically after Self-Deploy AutoPilot process completes, but its not auto logging. Any thought why KioskUser0 not auto logging automatically? Hi Mo, That can be many things, but something I often see is the device lock configuration that is interfering. Regards, Peter Hello Peter, We have Azure AD Joined devices in our enviornment which are migrated from source tenant to target tenant as part of carve out project. Recently we observed that post autopilot build completition when user tried to sign in to device they were prompted error as Sign in method not allowed. However, if we tried to login to device with local admins then it allows. Standard users not allowed to login, we do have AllowLocallyLogIn baseline policy deployed by security team but it contains Administrators and Users group both. Does on Azure AD joined devices this policy really gets validated when users trying to sign in with UPN ? This issue is not for all users but 10% users are facing, as a workaround when we reimported hash of thier device again and reimaged device then sign in was allowed (bit strange). Do you have any idea on this then please give some direction. Hi Suraj, How did you migrate the devices from source tenant to the target tenant? Regards, Peter I am seeing something similar for new devices. Again, not all, only a subset. quite often, the user can happily use the device for a period (a few days) then this occurs. LOgging onto the device locally, I am seeing the Allow Logon Locally being blank. very odd. This is using Windows 11 23H2 Hi Shaun, When that happens, do you see anything about (other) policies being applied and/or change? Regards, Peter I tried to do the restriction as in your procedure, but I got the error 65000 in intune. Since then, it has been impossible to connect with ALL the accounts on the computer. Do you have a solution to go back? Hi Simon, In that case, you should apply a counter policy with the default configuration. Regards, Peter I’ve had a similar issue. What would the correct counter policy be to reset the default logon configuration or do you have an article that details that? Hi Mike, Easiest is to check a different device an see what the default configuration is. Regards, Peter Leave a Comment Cancel replyNotify me of follow-up comments by email. Notify me of new posts by email. This site uses Akismet to reduce spam. Learn how your comment data is processed . 15 Group Policy Best Practices This is the most thorough guide to group policy best practices on the web. In this guide, I’ll share my recommended group policy settings and GPO management tips. These best practices will simplify GPO management, improve security, and GPO performance. Warning: Group Policy is not a one size fits all. Every Active Directory environment is different and there is no cookie-cutter solution for group policy. It is best to plan and test any changes to group policy before rolling it out to all systems. One small change could lead to major issues and impact critical business services. GPO Best Practices and Recommended SettingsI recommend reading the full list below as some best practices may not make sense unless you read them all.  1. Do Not Modify the Default Domain Policy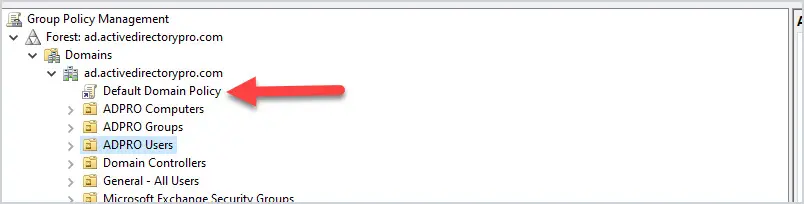 This GPO should only be used for account policy settings, password policy, account lockout policy, and Kerberos policy. Any other settings should be put into a separate GPO. The Default Domain Policy is set at the domain level so all users and computers get this policy. The Default Domain Policy is linked to the root of the domain. When you put multiple GPO settings into the default domain policy it becomes very difficult to troubleshoot and control GPO settings. It can also impact performance if the GPO has too many settings and every user and computer has to process them. It is best to use small GPOs (see tip #12) than to stuff everything into one big GPO. 2. Do Not Modify the Default Domain Controller Policy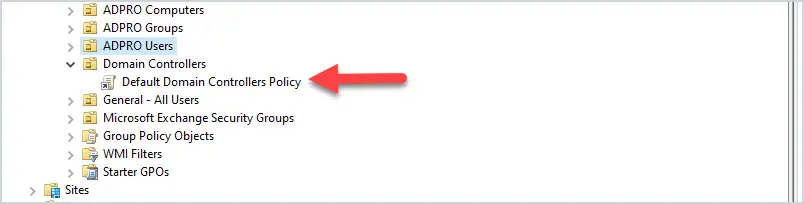 This GPO should only contain the User Rights Assignment Policy and Audit Policy. Any other settings to the Domain Controllers should be set in a separate GPO. The Default Domain Controller policy is linked to the Domain Controller OU. 3. Good Organizational Unit (OU) Design Will Make Your Job 10x EasierA good OU design makes it easier to apply and troubleshoot group policy. It is best to create an OU for computers and a separate OU for users. Then create sub-OUs on how you want to manage your objects. I typically organize objects by department and functionality. Example OU design: 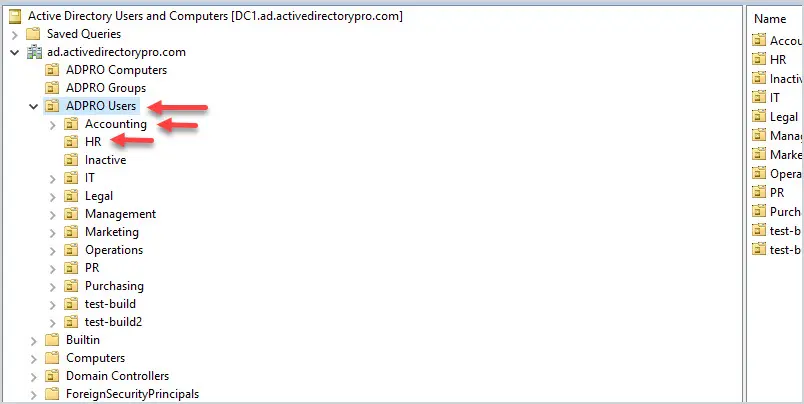 Putting users and computers in separate OUs makes it easier to apply computer policies to all the computers and user policies to only the users. Related: 21 Effective Active Directory Management Tips 4. Do Not Set GPOs at the Domain LevelThe only GPO that should be set at the domain level is the Default Domain Policy. Anything set at the domain level will get applied to all user and computer objects. This could lead to all kinds of settings getting applied to objects that you don’t want. It’s better to apply the policies at a more granular level. 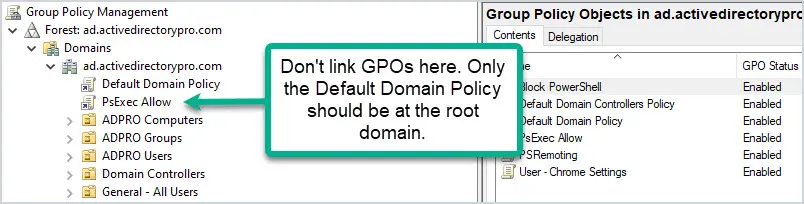 5. Apply GPOs to The Root OUApplying GPOs at the root of an OU will allow the sub-OUs to inherit these policies. This way you don’t need to link a policy to each individual OU.  If you want to exclude OUs or a group of users you have a few options.
Exclude Users using GPO Security Filtering. Let’s look at an example. I have GPO that disables saving passwords in the Chrome browser , the GPO is linked to all users. 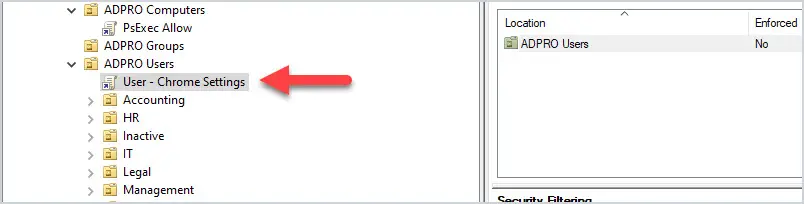 What if I have users in various departments that I don’t want this policy applied to? The solution is to use GPO security filtering. I create a security group, add users to the group, and then deny this group from applying the group policy. Now all users will get the GP except the users in the security group. 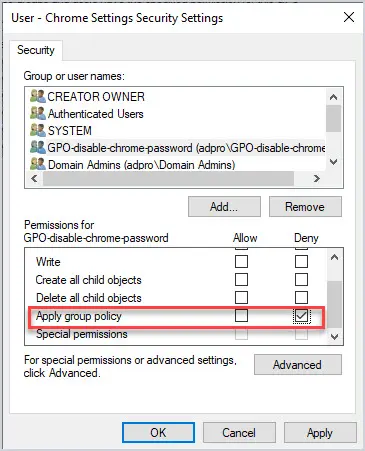 6. Avoid Using Blocking Policy Inheritance and Policy EnforcementIf you have a good OU structure then you can most likely avoid the use of blocking policy inheritance and using policy enforcement. I find it much easier to manage and troubleshoot group policies knowing neither of these is set in the domain. 7. Don’t Disable GPOsIf a GPO is linked to an OU and you don’t want it to be, delete it instead of disabling it. Deleting the link from an OU will not delete the GPO, it just removes the link from the OU. Disabling the GPO will stop it from being processed entirely on the domain, and this could cause problems. 8. Use Descriptive GPO NamesBeing able to quickly identify what a GPO is for based on the name will make group policy administration much easier. Giving the GPOs a generic name like “laptop settings” is too generic and will confuse people. It will also invite other admins to just dump any and all settings into a single GPO. Before are some descriptive GPO names:
Just by looking at the above GPO names, you have a pretty good idea of what they are used for. 9. Speed Up GPO Processing by Disabling Unused Computer and User ConfigurationsFor example, I have a GPO called browser settings, it only has computer settings configured and no user settings so, I have disabled the User configuration for this GPO. This will speed up group policy processing. To disable the computer or user configuration of a GPO:
 10. Use Loopback Processing for Specific Use CasesLoopback processing, in a nutshell, takes user settings and limits those settings to a computer the GPO is applied to. It is very useful but can also cause issues if used incorrectly. A common use of loopback processing is on terminal servers and Citrix servers. Users are logging into a server and you need specific user settings applied when they log into only those servers. You would need to create a GPO, enable loopback processing and apply it to the OU that has the servers in it. 11. Group Policy Change ManagementGroup policy can get way out of control if you let all your administrators make changes as they feel necessary. Change management can be dreadful and it can really slow projects down. I’m not saying all group policy changes should go through a formal change management process but they should be discussed with management and documented. One little GPO change could send a flood of calls to the helpdesk. It happens, so it’s best to discuss and document changes to GPOs. 12. Use Small GPOs to Simplify AdministrationIt can be easy to fall into the trap of stuffing everything into one GPO. I’m guilty of this too and it becomes a giant headache to manage. There really is no reason to do this, many small GPOs do not affect performance. Small GPOs make troubleshooting, managing, designing, and implementing 10x easier. Here are some ways to split up GPOs into smaller policies:
13. Best Practices for Group Policy PerformanceHere are some settings that can cause slow startup and logon times.
14. Group Policy Troubleshooting TipsKnow how to use the RSop and gpresult commands to verify and troubleshoot group policy. When troubleshooting you need a way to verify that GPOs are getting applied and check exactly what policies are applied. These two commands are a huge lifesaver. I’ve written a complete how-to article for each command so be sure to check them out. 15. Backup GPOsIf you are not backing up Active Directory or doing system state backup then you need to start backing up your GPOs. You may need to recover a deleted GPO or restore the settings from existing GPOs. See my complete guide on how to backup and restore group policy objects . To learn more about group policy check out my ultimate guide to group policy management . I hope you found this article helpful if you have any group policy questions leave a comment below. 56 thoughts on “15 Group Policy Best Practices”Any limit of object in OU for applying GPO with WMI? Is there a way to have a GPO only apply while a device is on battery power but not when it is plugged in. i.e. We have patrol vehicles that while the laptop is in the vehicle and plugged into power we cannot have the screen lock. However, once that machine is off power and on battery only then apply a screen lock after x minutes. You could try a WMI filter for batteryStatus = 1. https://learn.microsoft.com/en-us/windows/win32/cimwin32prov/win32-battery Thanks! very helpfull thank you from baku Would like to know what may be the cause of my DC administrator account not able to have elevated privileges? for context, I have set that users can not open cmd but when I tried using “run as” administrator, I am getting a message that says “C:\Windows\system32\cmd.exe The requested operation requires elevation” Also my users are getting removed from a security group that I created. eg: test user is a member of test_user_security group. Thanks in advance! Seems like the policy you set is restricting cmd. Remove the policy to test if that is the issue. Is there a template for complete block except for one program (remote app) and Explorer (not IE Explorer) to browse users private folder? Amazing guide, some things I already knew, but didn’t know the why. I still have a question, if an option has in Computers and Users, what is the best place to put? if an option has in Computers and Users, what is the best place to put it? Sorry, I don’t understand the question. For example in: Computer Configuration | Policies | Administrative Templates | Windows Componentes | AutoPlay Policies User Configuration | Policies | Administrative Templates | Windows Componentes | AutoPlay Policies You have the same options. I think putting for computers is better because it would apply to any user, but I’m not sure if it’s a best practice. Thanks again. It just depends if you want the policy to apply to all users that sign on to a computer, or specific users. For example, if you have a shared computer and need specific users to have a desktop shortcut you would use a user configuration. If you used a computer configuration all the users would get the shortcut. If all users need the policy then use computer configuration. excellent stuff Robert, please keep up the good work. and thank you for sharing your thoughts. Thanks Elias I have both my Win 10 citrix and win7 (soon to be win10) workstations on loopback/replace. I always get so much pushback from the network engineers about this. What is the best practice for applying a group policy which contains both User and Computer settings? Would you apply the policy to both the OU containing the users and the OU containing the computers or would you split the settings into 2 different policies (despite both policies being for the same cause). I recommend you seperate users and computers into their own OU. If that is not an option I would create two GPOs, 1 for the user settings and 1 for the computer settings. I already have separate OUs for Users and Computers. My question was what would you recommend is the best method if you have a GPO which contains settings for both Users and Computers. Would you split the Computer and User settings into 2 different GPOs (i.e. even if they are all for Internet settings) or would you apply the same GPO to both the Users and Computers OUs and therefore have a GPO with Computer settings on a User OU and a GPO with User settings on an OU for just computers? Yes, split it into two GPOs, 1 with just user settings and 1 with just the computer settings. Then you can disable the section that is not used. Best explanation for loopback processing I’ve ever seen. Always slightly confused about what it does. Not anymore 🙂 Glad it helped Robert, I deal with GPO management on a daily basis, in a very large environment. I agree with everything you’ve said. Here are a few things that have helped me tremendously, If you don’t want a GPO to apply to specific users or computers or groups for that matter, you can edit that GPO, go properties security and add the user, computer or group and select “DENY” apply group policy. Make sure you take advantage of adding comments to your GPO’s. Some GPO’s are doing alot and commenting them out will help you remember what they do and if there are any special nuance’s you need to take into consideration. George great tip. This is a great way to apply GPOs to very specific groups. I need to write a how-to on this, thanks for mentioning this. I find the practice of using Deny to be horrible! As soon as there is more than one administrator, or a change of admin employees (new person taking over), that kind of structure becomes rather confusing. If you need to use Deny, then you’ve designed the OU structure wrong… I agree that if it is not documented or communicated it can be a nightmare. But it can also be extremely useful for targeting specific users and computers and to deny it from all users. For example, I have a blanket firewall GPO that all users get for the basic FW settings. I have some users that need FTP on, I create a new security group and only apply this GPO to these users and deny it to all other users. I want to keep all the users in their department OU so moving to another OU is not a good option for this. Targeting a GPO to a security group is great but try not to let it get out of control. Could you please share the Steps & Process ? Great document, thank you Are GPO better or worse when trying to create and AD structure? Please Explain Good OU structure is important to implementing GPOs. It helps with properly targeting the right users and computers, troubleshooting and to ensure the policy gets applied. For examples, if you want to prevent certain users from creating a pst file in outlook the GPO needs to be applied to an OU with those users. If you apply the GPO to an incorrect OU it will either not get applied or get applied to the wrong group of users. Thank you this is awesome really! Thanks Brian I happen to come across your site searching for gpresults and bookmarked it. Quickly browsing through the various posts you’ve made, I like the summarized points! Complete newbie. I’m looking into tackling group policy and also like the rsop testing article. My question is whether to disable or delete the group policy – in some reading I came across a while back, it mentioned to disable a group policy as a precaution (for a period of time). Just in case, something does go wrong. Thank you for sharing your knowledge Not sure I understand your question. I would not recommend disabling or deleting the default GPOs or services on domain controllers. Thanks A lot for this post Thank you very much for spending so much time in putting this together. What suggestions do you have if the following rules have been broken and they need to be repaired? 1. Do Not Modify the Default Domain Policy 2. Do Not Modify the Default Domain Controller Policy I very seldom work with GPOs, have inherited a rat’s nest and I’m not sure where to start the unravelling process. On top of it all, there are built-in groups with members who don’t belong there i.e., specific Users are members of Administrators, Domain Admins and Enterprise Admins. I’d like to fix the problem without causing any major disruptions to developers (yes, developers are domain admins because that’s the way they wanted it to be). Would I be better off using third-party software to unravel and straighten out a mess? Thank you very much, John Nice tips, doing some already, but got some new also Thanks Maani very supporting great tips, i am installing AD, DHCP and DNS for a new organisation and this will definitely help in my planning and configuration. please also share tips on DNS and DHCP if possible. I’ll be working on a best practice guide for DHCP and DNS soon. Stay tuned. Could you elaborate a little more on why we need multiple gpos linked to an ou? Or are all the reasons there are? I suggest grouping similar policies into their own GPO as opposed to stuffing them into one big GPO. This will make troubleshooting, managing and applying policies much easier. I’ll give an example of turning the screensaver timeout on all the computers. If I put this policy into say the default domain policy it would get applied to all computers. Now if someone requests this policy be turned off on some specific computers there is no easy way to do that. If the screensaver policy was it’s own GPO then it becomes easy to filter it out for specific users and computers. It also makes it easier to report and see what policies you have when they are broken out. Does that make sense? really awesome Thanks Senthil. I hope you was able to put some of these tips to use. i’ve improved a lot my AD administration reading this article! Thank you Robert! Greetings from México! Greetings! Each year I seem to pick up a few good tips, I’m happy to share them. This is Brilliant ! Thanks Sujeeth Looks great. Thanks for this! Thanks Thomas Super Excellent!!!! Thank youuuuuu!! You’re welcome, Alex. Awesome guide! Thanks Mug! Thanks sofian! Leave a Comment Cancel replyUserRights Policy Deployment Using Intune | Group Policy ReplacementIn this post, you will learn how to deploy UserRights policies successfully. I am grateful to my colleague Mark Thomas for helping me fix the issue. You can use Intune to deploy security policies using out-of-box templates or Windows 10 custom policy CSP (UserRights Policy). I checked Intune Administrative templates , Security baselines , and box Device restriction policies to find options to deploy Windows 10 UserRights settings. I couldn’t see any out-of-box policies related to UserRights settings.
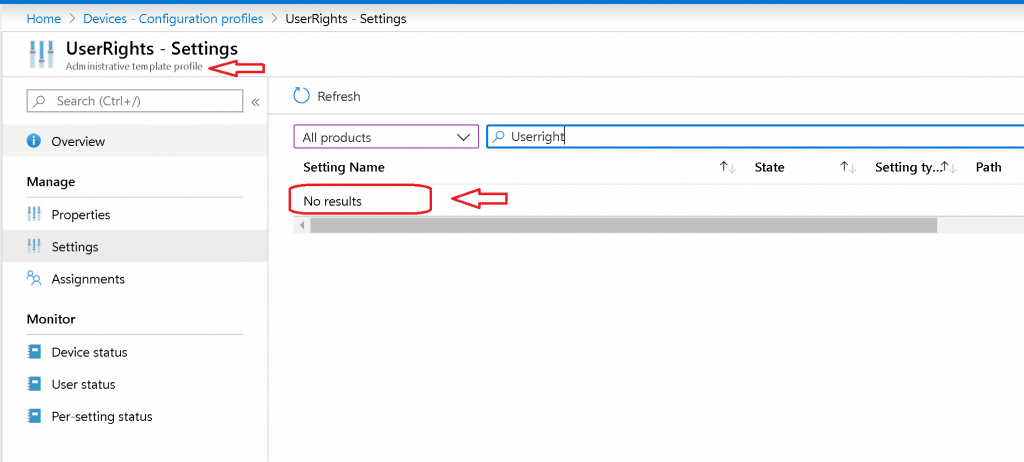 I have two options to deploy UserRights settings: 
Custom Windows 10 Policy CSPIn this post, you shall take an example of the specific policy CSP called: “./Device/Vendor/MSFT/Policy/Config/ UserRights / AccessFromNetwork “ I’m trying to provide “access from network” access to two user groups called “ Administrators ” and “ Remote Desktop Users .” XML Format – First TryI tried custom policy CSP using the Microsoft document recommendation here . 
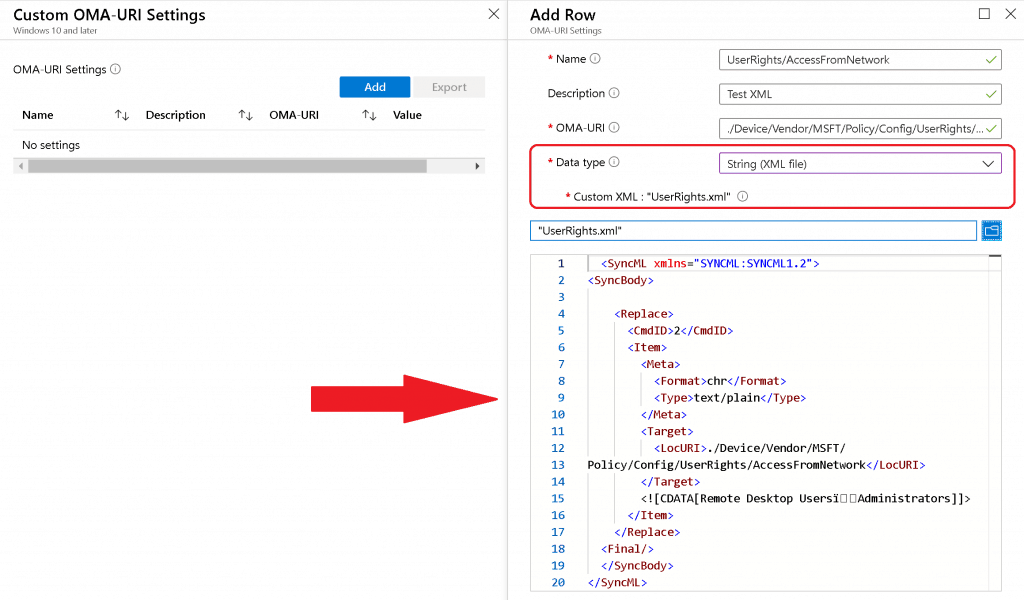 Sample XML for UserRights/AccessFromNetwork settings to add Remote Desktop UsersAdministrators ( note this symbol) groups The Data Type string (xml file) policy CSP settings failed with following error : 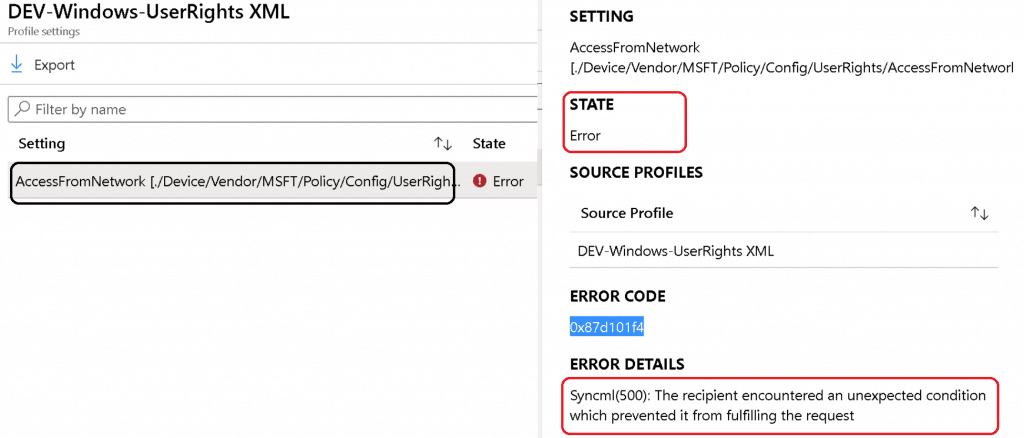 String Option – UserRight/AccessFromNetworkAs you saw above, the string XML file option to deploy policy CSP failed. Next, try Data Type -> String with Windows 10 policy CSP. I tried to look at the GitHub thread and use the following settings to deploy the UserRight/ AccessFromNetwork policy CSP. 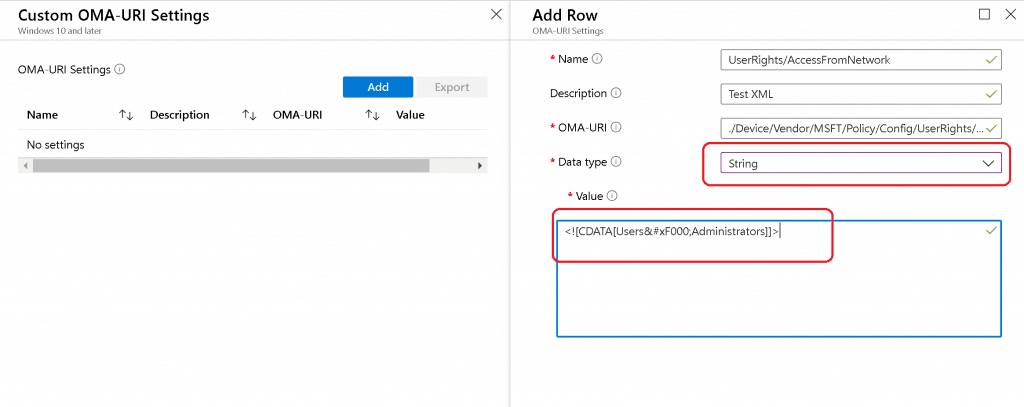 The above setting was successfully applied on the Windows 10 device, but Intune shows an error -2016281112 (Remediation failed) . These error details are also explained in the above GitHub thread. ASCII Value ( ) Issues with UserRights CSPThis is the option where my colleague Mark Thomas came to the rescue. Mark helped me FIX the Windows 10 custom policy CSP ASCII character-related issue. NOTE – This ASCII value ( ) mismatch is also discussed in the GitHub thread. String Value to provide “UserRight/AccessFromNetwork” access to the following groups:
The following are the third and final options that were successful. 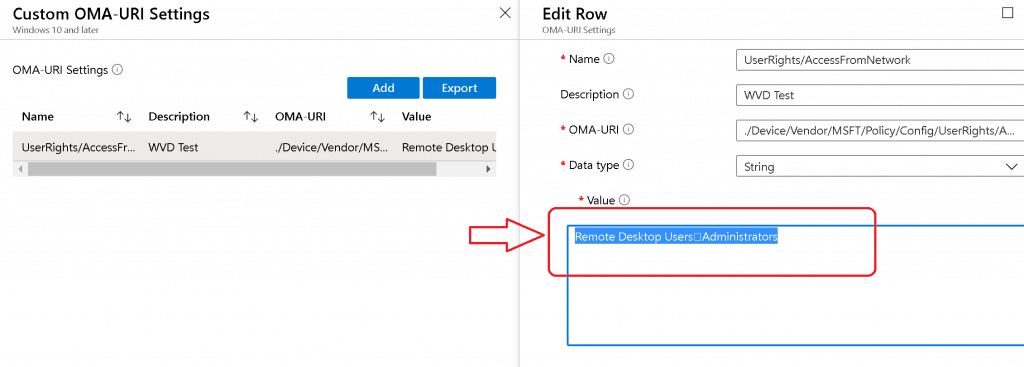 Policy CSP Settings Intune: Results – UserRights Policy Deployment Using Intune | Group Policy ReplacementThe Windows 10 custom policy CSP was successfully deployed without group policy settings. Happy modern management! 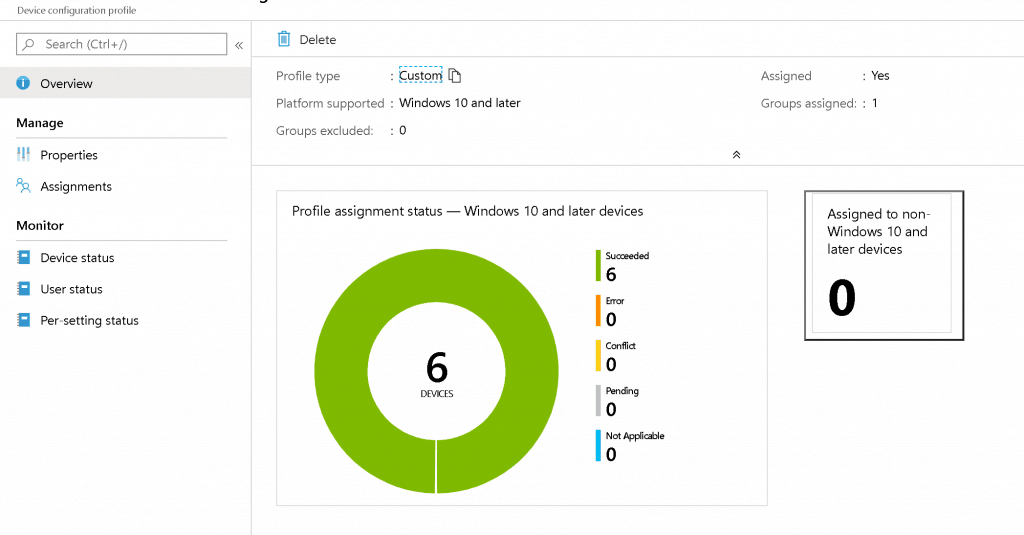 We are on WhatsApp . To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp . Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc. 10 thoughts on “UserRights Policy Deployment Using Intune | Group Policy Replacement”Works like a charm, thanks for going through all the pain for us. 🙂 Great to know … thank you for the feedback Hi, where and how do I find the endpoint settings defined from Intune? For GPO, were the tools gpresults and rsop? Is there something similar for Intune? Thanks David Diagreport from the client might help you Hi Anoop, I am trying to restrict few user groups from interactive login to AzureAd joined devices and was exploring UserRights/DenyLocalLogOn. I did give the objectID of the azure ad group in the string but it didn’t work. Have you tried this? Also, is there any other better way to handle this? Did you ever find a way to deny a local login using a CSP? I was trying to limit anyone in the local Guests group on the machine from logging in. This was my final setting that applied successfully after reading this article. Name: DenyInteractiveLogonRight OMA-URI: ./Device/Vendor/MSFT/Policy/Config/UserRights/DenyLocalLogOn Data type: String Value: Guests Do you know if there is a way to include multiple domain users in this userrights CSP? I tried with the separators included in this article but it is not working. Thanks a lot How do I add an Azure AD group to this list? I have tried just about everything, and cannot figure out how to do it. Same for me, I was able to add specific AAD user but not an AAD group.. Tried with SID but does not work It doesn’t appear to be possible to use a AAD group in the assignment which is terrible really. This should be a standard function Leave a Comment Cancel replyThis site uses Akismet to reduce spam. Learn how your comment data is processed . Stack Exchange NetworkStack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers. Q&A for work Connect and share knowledge within a single location that is structured and easy to search. How can I locate Registry key for Group policy settings?How can I locate the registry entry for the below values
under Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\User Rights Management . I tried the below 3 ways.
End goal is to automate configuration thru Powershell [ Set-ItemProperty ]
3 Answers 3As you can see in the Group Policy Settings Reference Guide (see your 1st link; in particular, Windows10andWindowsServer2016PolicySettings.xlsx document ), most of security settings (e.g. User Rights , Password Policy , Audit Policy etc.) are not registry keys . Those are stored in the Secedit.sdb database. For your task, you can use Microsoft's secedit command line tool (at least, export and import): secedit Configures and analyzes system security by comparing your current configuration to specified security templates. Syntax secedit [/analyze /db <database file name> /cfg <configuration file name> [/overwrite] /log <log file name> [/quiet]] [/configure /db <database file name> [/cfg <configuration filename>] [/overwrite] [/areas [securitypolicy | group_mgmt | user_rights | regkeys | filestore | services]] [/log <log file name>] [/quiet]] [/export /db <database file name> [/mergedpolicy] /cfg <configuration file name> [/areas [securitypolicy | group_mgmt | user_rights | regkeys | filestore | services]] [/log <log file name>]] [/generaterollback /db <database file name> /cfg <configuration file name> /rbk <rollback file name> [/log <log file name>] [/quiet]] [/import /db <database file name> /cfg <configuration file name> [/overwrite] [/areas [securitypolicy | group_mgmt | user_rights | regkeys | filestore | services]] [/log <log file name>] [/quiet]] [/validate <configuration file name>] Parameters Secedit: analyze Allows you to analyze current systems settings against baseline settings that are stored in a database. The analysis results are stored in a separate area of the database and can be viewed in the Security Configuration and Analysis snap-in. Secedit: configure Allows you to configure a system with security settings stored in a database. Secedit: export Allows you to export security settings stored in a database. Secedit: generaterollback Allows you to generate a rollback template with respect to a configuration template. Secedit: import Allows you to import a security template into a database so that the settings specified in the template can be applied to a system or analyzed against a system. Secedit: validate Allows you to validate the syntax of a security template. Answer : Look for the below keys/entries under [Privilege Rights] section in the exported configuration file (you can add/change them easy using Powershell):
Read (and follow) Windows Security Baselines as well: A security baseline is a group of Microsoft-recommended configuration settings that explains their security impact. These settings are based on feedback from Microsoft security engineering teams, product groups, partners, and customers.
You can use GPSearch resource to get corresponding keys: https://gpsearch.azurewebsites.net/ Also, you can try to apply the policy and track the changes in the registry with Process Monitor: https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
While this answer isn't applicable for the policies specified in the question, I just wanted to throw https://admx.help in the ring for finding any registry keys relating to administrative templates policies. I prefer it over GPSearch mentioned by batistuta09 as it is much easier to read the information relating to the key/s, in my opinion. To locate a desired key, scroll to and click on your OS of choice, then the policy categories trees for administrative templates we're all familiar with will appear on the right-hand side to be explored. For example, I wanted to locate any keys associated with enabling the policy "Specify settings for optional component installation and component repair" locally on my Windows 10 machine (Local Computer Policy > Computer Configuration > Administrative Templates > System). On the website home page, you navigate as follows: Windows 10 and Windows Server 2016 > Administrative Templates (Computers) > System > Specify settings for optional component installation and component repair Once the policy is selected, any associated keys and their details are displayed clearly. 2022 edit: Updated url from getadmx.com to admx.help. Thanks, @Henke. You must log in to answer this question.Not the answer you're looking for browse other questions tagged powershell group-policy windows-server-2016 automation ..
Hot Network Questions
Welcome to Microsoft Forms!
Explore templates
This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Allow log on locally - security policy setting
Describes the best practices, location, values, policy management, and security considerations for the Allow log on locally security policy setting. This policy setting determines which users can start an interactive session on the device. Users must have this user right to log on over a Remote Desktop Services session that is running on a Windows-based member device or domain controller. Note: Users who do not have this right are still able to start a remote interactive session on the device if they have the Allow logon through Remote Desktop Services right. Constant: SeInteractiveLogonRight Possible values
By default, the members of the following groups have this right on workstations and servers:
By default, the members of the following groups have this right on domain controllers:
Best practices
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment Default valuesThe following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy's property page.
Policy managementRestarting the device is not required to implement this change. Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. Modifying this setting might affect compatibility with clients, services, and applications. Use caution when removing service accounts that are used by components and by programs on member devices and on domain controllers in the domain from the default domain controller's policy. Also use caution when removing users or security groups that log on to the console of member devices in the domain, or removing service accounts that are defined in the local Security Accounts Manager (SAM) database of member devices or of workgroup devices. If you want to grant a user account the ability to log on locally to a domain controller, you must make that user a member of a group that already has the Allowed logon locally system right or grant the right to that user account. The domain controllers in the domain share the Default Domain Controllers Group Policy Object (GPO). When you grant an account the Allow logon locally right, you are allowing that account to log on locally to all domain controllers in the domain. If the Users group is listed in the Allow log on locally setting for a GPO, all domain users can log on locally. The Users built-in group contains Domain Users as a member. Group PolicyGroup Policy settings are applied through GPOs in the following order, which will overwrite settings on the local computer at the next Group Policy update:
Security considerationsThis section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation. VulnerabilityAny account with the Allow log on locally user right can log on to the console of the device. If you do not restrict this user right to legitimate users who must log on to the console of the computer, unauthorized users could download and run malicious software to elevate their privileges. CountermeasureFor domain controllers, assign the Allow log on locally user right only to the Administrators group. For other server roles, you may choose to add Backup Operators in addition to Administrators. For end-user computers, you should also assign this right to the Users group. Alternatively, you can assign groups such as Account Operators, Server Operators, and Guests to the Deny log on locally user right. Potential impactIf you remove these default groups, you could limit the abilities of users who are assigned to specific administrative roles in your environment. If you have installed optional components such as ASP.NET or IIS, you may need to assign the Allow log on locally user right to additional accounts that are required by those components. IIS requires that this user right be assigned to the IUSR_ <ComputerName> account. You should confirm that delegated activities are not adversely affected by any changes that you make to the Allow log on locally user rights assignments. Related topics
Additional resources |
COMMENTS
User rights are managed in Group Policy under the User Rights Assignment item. Each user right has a constant name and a Group Policy name associated with it. The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy ...
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
They include account policies, local policies, user rights assignment, the Windows firewall, software restrictions, and so on. There are several ways to configure security policy settings. The most common are: Group policy objects (GPO) - Used in Active Directory domains to configure and regularly reapply security settings to multiple computers.
This video summarizes the functionality of each of the different User Rights Assignment Policies and discuss recommended policy settings and their impact on ...
1. Press the Win+R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2. Expand open Local Policies in the left pane of Local Security Policy, click/tap on User Rights Assignment, and double click/tap on the Allow log on locally policy in the right pane. (see screenshot below) 3.
Each computer has its own user rights assignments. In particular this means you should be cognizant of rights assignments on member servers which may easily differ from the rights assignments you find on your domain controllers. To centrally control user rights assignments on computers throughout your domain use group policy. Logon rights
4. You cannot edit this User Rights Assignment policy because this setting is being managed by a domain-based Group Policy. In this case, the domain Group Policy setting has precedence and you are prevented from modifying the policy via Local Group Policy. To modify this policy, either:
Personal File Server - Get-UserRights.ps1 Alternative Download Link. or. Personal File Server - Get-UserRights.txt Text Format Alternative Download Link. In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
On the Configuration settings page, as shown below in Figure 2, perform the following actions. Click Add settings and perform the following in Settings picker. Select User Rights as category. Select Allow Local Log On as setting. Specify the required users and local groups - all on separate lines - and click Next.
This GPO should only contain the User Rights Assignment Policy and Audit Policy. Any other settings to the Domain Controllers should be set in a separate GPO. The Default Domain Controller policy is linked to the Domain Controller OU. 3. Good Organizational Unit (OU) Design Will Make Your Job 10x Easier.
Group Policy if the device is domain joined or Hybrid Azure AD Joined. Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Custom Windows 10 policy CSP using Intune for Azure AD joined devices. Custom Windows 10 Policy CSP. In this post, you shall take an example of the specific policy CSP called:
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, click/tap on User Rights Assignment, and double click/tap on the Change the system time policy in the right pane. (see screenshot below) 3 Click/tap on the Add ...
Perform volume maintenance tasks. Lock pages in memory. under Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\User Rights Management . I tried the below 3 ways. Find the Registry key for corresponding Group Policy : (1)Final Link broken (2)Couldn't locate above in reference guide or MSDN doc.
Don't create a separate account and assign this user right to it. Location. Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Default values. The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on ...
Microsoft Forms is a web-based application that allows you to: Create and share online surveys, quizzes, polls, and forms. Collect feedback, measure satisfaction, test knowledge, and more.
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Default values. The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy's property page.
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, click/tap on User Rights Assignment, and double click/tap on the Allow log on through Remote Desktop Services policy in the right pane. (see screenshot below)